Enhancing Security Through Network Topology
| Background.
This web page will focus on the presentation of some network topologies
that improve security. Secure topologies are designed using
firewalls. Firewalls perform two very
basic functions blocking some traffic and permitting some traffic.
Firewalls can be configured to emphasize one or the other to varying
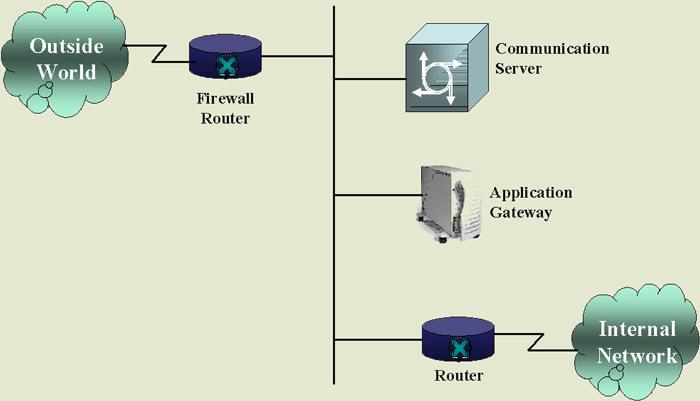
extents. Probably, the simplest firewall configuration is represented in the following diagram. |

| It is important to notice in this sort of
design, the firewall can very easily become a bottleneck if it has
insufficient throughput capacity or reliability. Even some people configure this sort of system at home with just a server, a couple printers and a couple computers. It can be very important to make sure that people from the outside cannot gain undesired access to your resources. A more sophisticated, yet quite common configuration is represented in the following diagram. |
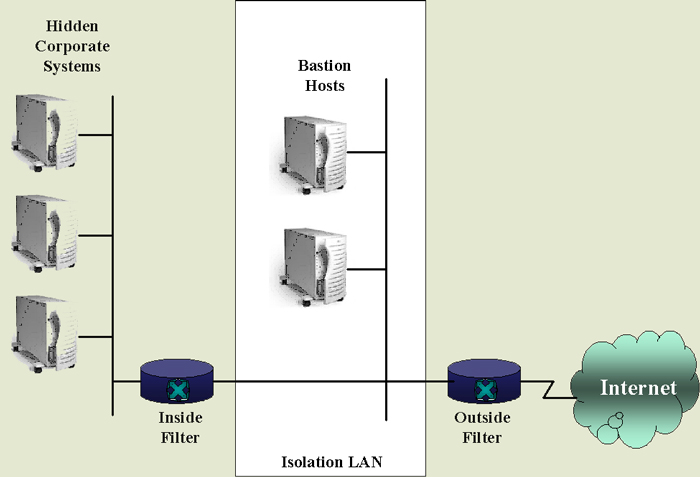
The three main portions to this firewall system as
outlined in Teare are
Some example services that may be provided to the outside world that are located on the bastion hosts in the isolation LAN follow.
The isolation LAN has a unique network number that differs from the corporate network number. Only the isolation LAN is visible to the outside world and advertises its services only to the isolation LAN. The following lists some rules for the three part firewall system.
Particular firms make particular routers with enhanced properties for security such as CISCO PIX Firewalls. |