Firewalls
| Introduction.
Firewalls are special routers that
intercept and control traffic between a private network and public
networks, especially on the Internet. A normal router might serve
as a firewall if it is configured so that all traffic in and out of the
private network must flow through it. But in and of itself, this
is not adequately secure so that other features need to be implemented
to increase the firewall's viability.
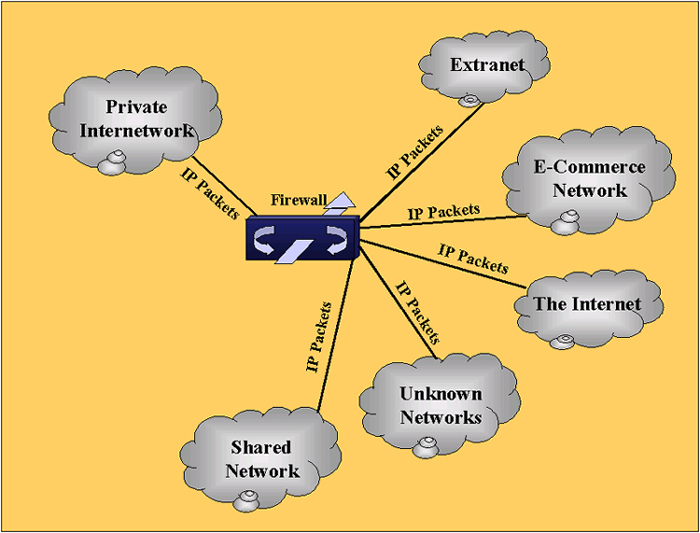
It is also important to remember that firewalls work both to keep certain traffic outside of a particular network and certain traffic inside the network. For example, everyone is aware the dangers that e-mails containing viruses present and a lot of effort is expended to keep these out. On the other hand, if people are shopping at the on-line store you just developed you don't want them to also be able to gain access to things like your pay and social security number. The following image represents the sort of funnel point required to implement a firewall. |

| Firewalls chart a defensive landscape and rely on
policy to determine what sorts of messages should get through and with
what other subnetworks. Depending on the operating system, the
classification of these outside networks can be quite rigid or flexible.
The simplest form of network security technology is an access list. These lists restrict certain traffic from gaining access into or outside the private network. They can filter packets based on three criteria:
While much more can be said about these access lists, some other features you might want to have from your firewall are
CISCO Routers. All of the above features and more can be can be obtained from Cisco routers by adding their IOS Firewall feature set. Thus you can make use of equipment you already have. Though the standard configurations have an inside router between the internal network and the firewall and another router outside the firewall connecting to the rest of the Internet. This is illustrated in the following diagram. |
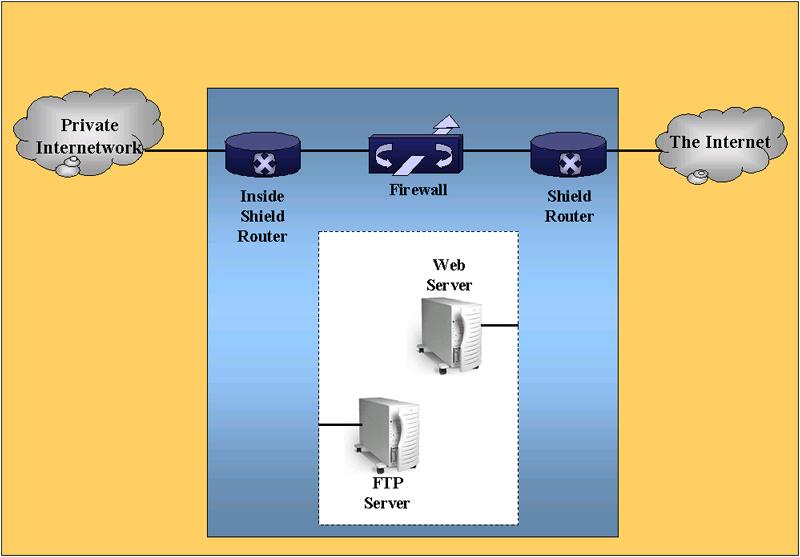
| Obviously, these sorts of things can be configured in a
number of different ways, depending on your situation. For
example, maybe you only want one router with firewall capability
performing all of the shielding, routing and filtering functions.
CISCO Firewalls. Cisco also offers a several lines of products that are dedicated to firewall function. These make use of a different technology than just enhanced IOS. These products are called Cisco Secure PIX Firewalls. They have three special advantages over the IOS implementation.
Without going into a lot of details, the following table summarizes Cisco PIX firewalls. |
| Cisco Secure Pix Firewall 506 |
Cisco Secure Pix Firewall 515 |
Cisco Secure Pix Firewall 520 |
Cisco Secure Pix Firewall 525 |
Cisco Secure Pix Firewall 535 |
|
| Market | SOHO | Small/medium business and remote offices | Large enterprises with complex high end traffic | Enterprise and service providers | Enterprise and service providers |
| Processor | 200 MHz | 200 MHz | 233 MHz | 600 MHz | 1 GHz |
| RAM | 32MB | 32 - 64MB | 128MB | < 256MB | 1GB |
| Interfaces | Dual integrated 10BaseT Fast Ethernet |
Dual integrated
10/100BaseT Fast Ethernet |
Dual integrated
10/100BaseT Fast Ethernet |
Dual integrated
10/100BaseT Fast Ethernet |
Eight Gigabit Ethernet or 10/100 Fast Ethernet single VAC |
| Connections | 10 Mbps throughput | 120 Mbps throughput; 50,000 - 100,000 concurrent connections |
370 Mbps throughput; 250,000 concurrent connections | 370 Mbps throughput; 280,000 concurrent connections | 1 Gbps throughput; 500,000 concurrent connections; 2,000 simultaneous VPN tunnels |
| NIC Support | Ethernet | Fast Ethernet | Fast Ethernet, Token Ring, FDDI | Fast Ethernet, Gigabit Ethernet, Token Ring, FDDI | Fast Ethernet, Gigabit Ethernet, Token Ring, FDDI |
| This information will be updated intermittently. In addition, I will post some offerings from CISCO competitors while trying to focus on those with largest market share. Any assistance in this will be greatly appreciated. |