
The OSI Model Revisited
| Models. In a
previous web page we already talked about the
OSI Reference Model. Now we will revisit it more in
accordance with some other sources. I'm hoping that returning to
the topic will improve your sense of "gestalt" with the model. The OSI - Open System Interconnection Model was developed by the ISO - International Organization for Standardization. The ISO acronym seems out of order because the name is translated from French. As we mentioned previously the model is made up of seven layers, each representing a step in the network transmission process. The following image gives a representation. |

| The protocols that make up the protocol suite operate
at different layers. Each layer focuses on a particular aspect of
what needs to be done in order to make computer network communications
effective. Reiterating what has been said in the previous page, as the data passes through each layer before transmission it adds its own header with information that will have meaning to its corresponding layer at the receiving device. Peer Layers. We will say a bit more about peer layers between the transmission and receiving devices. The following diagram should assist this discussion. |
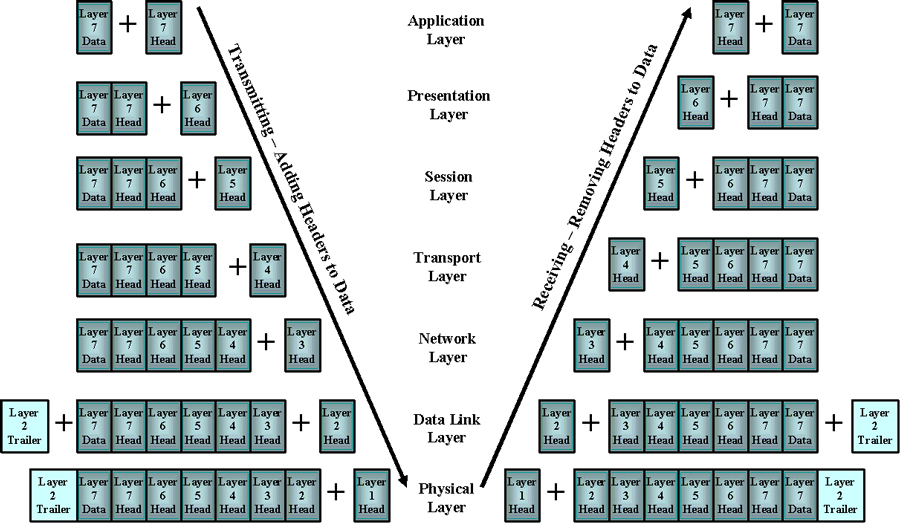
| At the transmission source the headers are added on
with appropriate information at each layer. It starts with receiving
the data from some application at the application layer. As it
travels down the layers it is encapsulated within a larger unit as each
layer adds its own information. The Data Link Layer does some error
checking and adds the trailer. After it is handled by each layer it
is transmitted. After it is received, the process occurs in reverse. Each layer takes its header and other appropriate information. The Data Link Layer repeats the error checking and compares what is in the trailer to what is computed. Unfortunately, some sources state that layer 1 doesn't add a header, but other sources say that it does. I am trying to resolve this. An older book by Littlejohn Shinder published by Cisco says that it does. But I need to check Forouzan, a respected source for Electrical Engineers. Now we will give a more involved discussion of what each layer does than we had in the previous web page. The Application Layer. The application layer provides for the interaction between the user's application program and the network. Protocols that function in this layer perform functions such as
As you might expect there are other application layer protocols. HTTP for the world wide web is one of the most pervasive. It is important to not confuse the actual application programs with the protocols of the same name. For example, there are a large variety of FTP programs such as CuteFTP, WS_FTP, FTP Explorer and on and on. These programs all make use of the FTP protocol to run, but they provide their own features when implemented. The Presentation Layer. The application layer receives data from the user application and passes it down the stack to the presentation layer. As the name suggests this layer handles issues like packaging and/or presentation of the data. The following list surveys a few possibilities.
The presentation layer on the receiving device is responsible for uncompressing, decrypting and otherwise translating data into a format appropriate for an application and presenting it to the application layer. Many gateways operate at the presentation layer, some consider this to be a necessary condition for a device to be called a gateway. More generally, a gateway is a device or program that serves as a connection point between two different networks. But the term gateway has tended to shift in meaning, which we will discuss when we get to routers. Redirectors generally operate at this level. Redirectors are software that determine whether a request should be handled by a local network device and redirect input/output appropriately. The Session Layer. The protocols operating at this layer have the purpose of establishing a one-to-one session between the sending and receiving computers. This layer constructs and deconstructs dialogs from application to application. It also provides for checkpointing to synchronize the data flow between applications. Checkpointing involves putting markers in the stream of data. If there is a failure in the flow then only data from the most recent marker needs to be retransmitted. Another thing controlled by the session layer is whether the transmission is sent in half duplex or full duplex. Transmissions in which both the ends of the communication can transmit at the same time are called full duplex. While information can still flow in both directions during half duplex transmissions, only one side can transmit at a time. The session layer is also responsible for establishing the rules for data exchange. It can also perform security functions and name recognition. Some fairly well known session layer protocols include the following.
The Transport Layer. This layer is primarily associated with end-to-end error control and flow control. The transport layer protocols handle the structuring of messages. The transport layer keeps track of things such as
There are two main types of protocols used
TCP - Transmission Control Protocol, the Internet standard, is a connection oriented protocol. It works in the transport layer of the transmission protocol. UDP - User Datagram Protocol is a connectionless protocol that is more commonly used on the Internet for most systems work since it requires less overhead. Connectionless protocols work more like the US Postal Service where you send a letter assuming it will reach the destination to which it is addressed, but there is no automatic verification mechanism. Connection oriented protocols are more like using certified mail with a return receipt requested. This way you are notified when the package is received. The transport layer also provides name resolution which involves resolving computer/host names to logical network addresses. Thus the DNS - Domain Name System operates at this layer. The transport layer also works to help coordinate ports and sockets. For example, let's assume you are receiving an e-mail message, while receiving a download through FTP. These will be both go to the same network address, but will go to different ports on your computer. Some of the more well known ports are for
The Network Layer. This layer is responsible for getting the data packets to their destination via routers. Most routing protocols operate at the network layer. There are also switches that operate at this layer. The Data Link Layer. This is the second layer in the OSI Model. It has actually been divided into the two sublayers in the following list. Both switches and bridges are typically layer two devices.
The MAC sublayer handles physical addressing issues using what are often called MAC addresses. On Ethernet and Token Ring networks these are hexadecimal numbers permanently burned into the chip on each NIC. These MAC addresses are 12 hexadecimal digits arranged in pairs on Ethernets. They represent things such as manufacturer and card. In theory, there should be no two cards with the same MAC address. But there have been some errors in this. Though this is going to cause a problem only if the duplicate addresses are on the same network. The LLC layer is associated with the logical topology of the network, not the physical topology. This sublayer is responsible to providing an interface between the MAC sublayer and the network layer above it. The Physical Layer. In this layer the data, headers and trailer are translated into signals that can be transmitted on a network. The physical layer turns everything into electrical impulses or pulses of light or something else. This layer is focused on signal issues, including those in the following list.
You also need to be considering the impact of choices about NICs, switches and/or hubs and their impact on operations. For example, among other things, the NIC must be conform to the requirements placed by the
The network transceiver, which is likeliest to be a hub or switch, also must conform to the above requirements. |