Web Traffic Interception and
Deception
Man in the Middle
TCP/IP Hijacking
Replay Attacks
Interception and Deception.
TCP/IP protocols were not really designed with security in mind. Web Traffic Interception and Deception
can occur in a large variety of ways. Three of the most common
are listed below.
Web traffic can be sniffed and/or spoofed in a variety of ways. There are such a variety of attacks that it really is very difficult to cleanly classify them. But these attacks have some aspects in common in that they do the following.
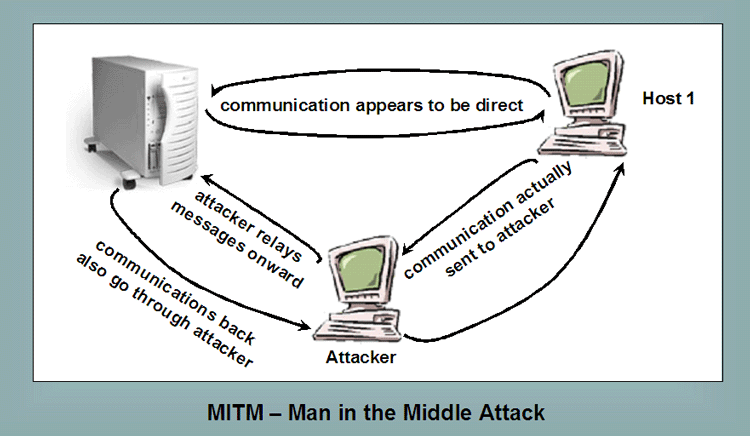
In the following sections we will get into more detail about each of the three attacks we are going to discuss. MITM. MITM is an acronym for Man in the Middle. MITM attacks occur when an attacker is able to place themselves in between two communicating hosts. From the point of view of the attacker, this can usually be best accomplished by compromising the router of the target host. Though, it is also often accomplished by compromising the router near to the initiator of the session. After compromising a particular router in this way the attacker can make sure all traffic is routed through the attacker's devices. Once this sort of situation is developed the attacker can observe all traffic before relaying it on. This also gives the attacker the capabilities to modify or block particular traffic. in both directions. MITM attacks are much more easily accomplished on Telnet sessions. In order to be accomplished on most other Internet traffic where packets are involved, the attacker needs to be able to fake sequence numbers like we talked about in the previous webpage on spoofing. The following diagram gives a visual representation. |

| The amount of information that can be gathered
and/or altered in an MITM attack can be greatly limited if the
traffic is encrypted. But, never the less, an attacker can
still observe whether particular hosts are communicating. One of the few ways that a MITM attack can occur on encrypted traffic is for the MITM to intercept the key that is going to be used for the encryption if one is passed. Depending on the type of relationship between the two communicating hosts that the MITM is trying to penetrate, a public key along with the type of encryption to be used might be sent very near the beginning of their interaction. If the MITM can intercept this then the attacker will stand much greater chances of being able to do what they want. MITM attacks are generally started right at the beginning of an effort to communicate on a network. Replay Attacks. A replay attack is where an attacker captures a portion of a communication between two parties and retransmits it at a later time. For example, an attacker might choose to replay a series of commands, codes and messages used to execute a financial transaction. Replaying this transaction would cause it to be executed more than once which would be very troublesome for the more legitimate parties involved. The best way to prevent and/or deter replay attacks is to make use of
TCP/IP Hijacking. TCP/IP Hijacking refers to taking control of an already existing session between a client and a server. This can also be called session hijacking. There are some advantages to intercepting packets without trying to penetrate a particular administrative domain/network. The main one is that an attacker can intercept packets TCP/IP Hijacks are usually directed against web or telnet sessions. In the previous webpage on spoofing we had some discussion about how an attacker needs to be able to fake sequence numbers when spoofing. This discussion also applies to TCP/IP Hijacking. Some appoaches that can be used to perform TCP/IP Hijacking follow.
Prevention. One of the likeliest ways to deter MITM, Replay, TCP/IP Hijacking or other related sorts of spoofing attacks is to make use of TCP sequence numbers that are as close to truly random as possible. Even though the numbers are incremented within sessions, in large part to help reorganize packets and communicate, the initial sequence numbers can be generated to simulate random numbers making them much less predictable. Another approach is to make use of well encrypted sessions. More will be added. |