VPN - Virtual Private Network
| VPN.
VPN stands for
Virtual Private Network. The word
virtual is used because the privacy and security are obtained
on the Internet and/or other networks through encryption.
Since the contents of the packets flowing in a VPN are encrypted
everything will be secure from most other users on an open network. You will often hear the word "tunneling" used to characterize VPNs. I think this is a misleading use of the word since the word tunnel makes it sound like there is a set path between the communicating parties. The reality is that the packets are still routed over the Internet or other network using a variety of paths based on routers decisions for each packet. VPNs can be created using any of the following sorts of devices
But handling the encryption/decryption increases operating overhead on devices implementing VPN, so administrators are making more use of more specialized devices. VPNs use a variety of protocols to support encrypted interactions. The following lists the most commonly used.
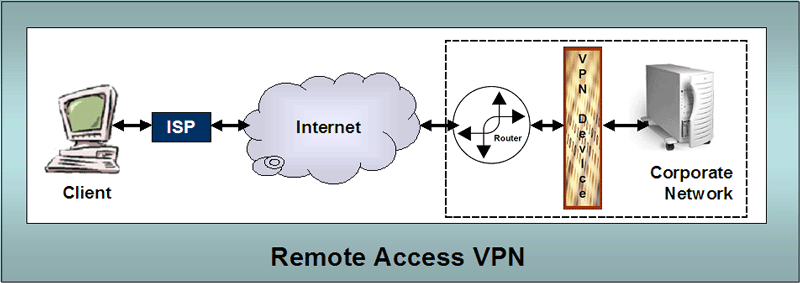
IPSec is the most popular, followed by L2TP and then PPTP. We discuss these protocols in other webpages this week. Remote Access VPNs. One of the most common uses of VPNs relates to remote access for users. The following diagram illustrates the basic flow of packets and connection. |

Typically the user will do one of the
following
In order to use the VPN services provided by the network, the user must have the appropriate client VPN software installed on their computer to interact with the VPN device in the corporate network to handle the encryption/decryption and other communication aspects. Intranet VPNs. One of the other most common uses for VPNs is to connect offsite offices or branches of an organization. The following diagram gives a general representation of what is involved. |
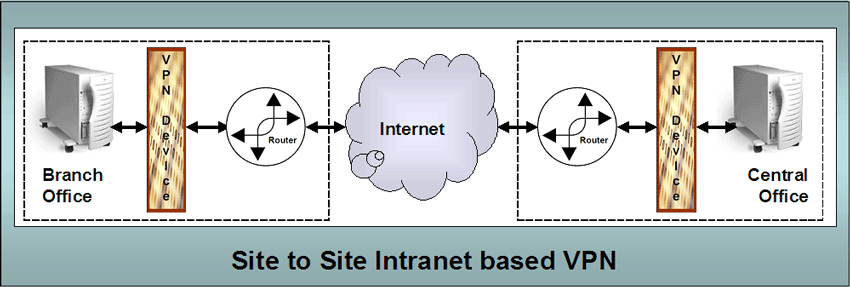
| This way, any two sites in a larger enterprise
network can be reasonably securely connected using the Internet.
This means the organization will not need to purchase/lease
dedicated lines, time on dedicated lines or other kinds of
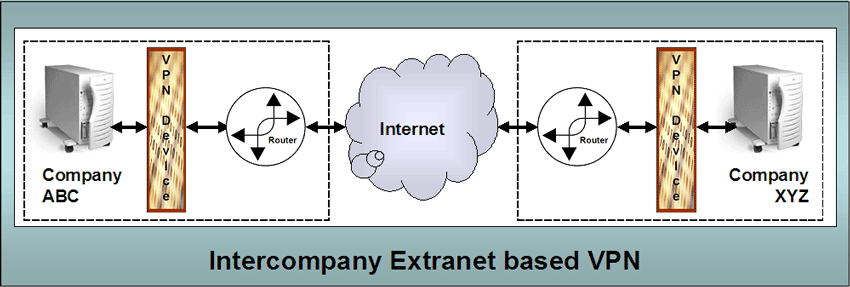
interconnectivity. Extranet VPNs. It should make sense that if a single organization can make use of VPN to interconnect and create their own Intranet, then two or more organizations can create an extranet. The following diagram represents an extranet VPN. |
Improving Security. Remember it is
always important to do things like the following to enhance the
security of a VPN.
More will be added. |