SYN Attacks
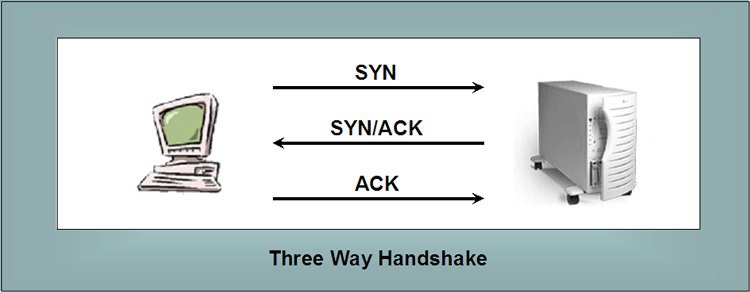
| Some Background. SYN
attacks are some of the most frequent DoS or DDoS attacks.
They take advantage of some of the underlying structure for
communications in TCP/IP. Communications between two hosts via the Internet rely on certain patterned exchanges. One of these is called the three way handshake and is illustrated in the following diagram. |

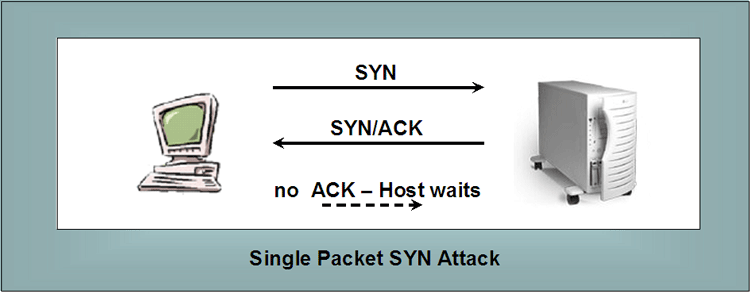
A SYN attack relies on this underlying communication protocol to disrupt the flow of communications with the host the attack is targeting. It largely relies on keeping the host under attack waiting for the ACK so that it is less capable of doing other things. This is illustrated in the following diagram. |
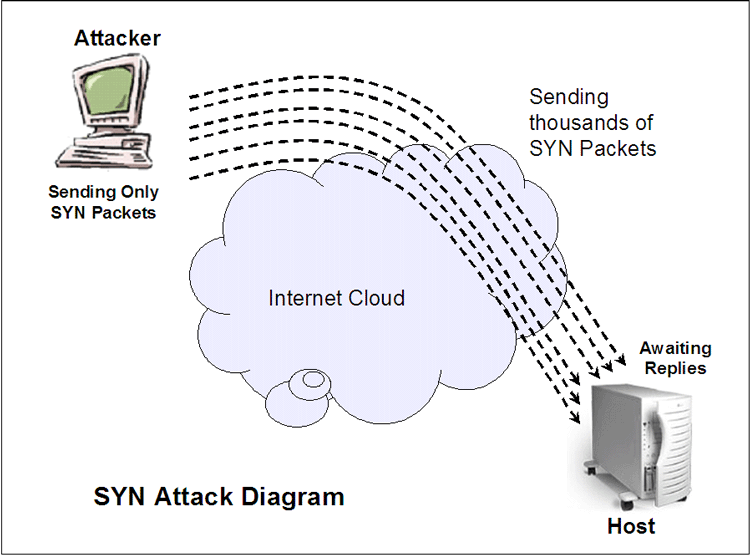
| This whole situation can be debilitated and
exacerbated further if the attacker sends a large number of SYN
packets so that the attacked host commits more and more resources to
wait for ACK packets that will never arrive. This is illustrated in the following diagram. |
| DDoS SYN Flood. A DDoS SYN Flood makes use of the SYN flood or attack via a DDoS attack. The following diagram discusses these in more detail. |
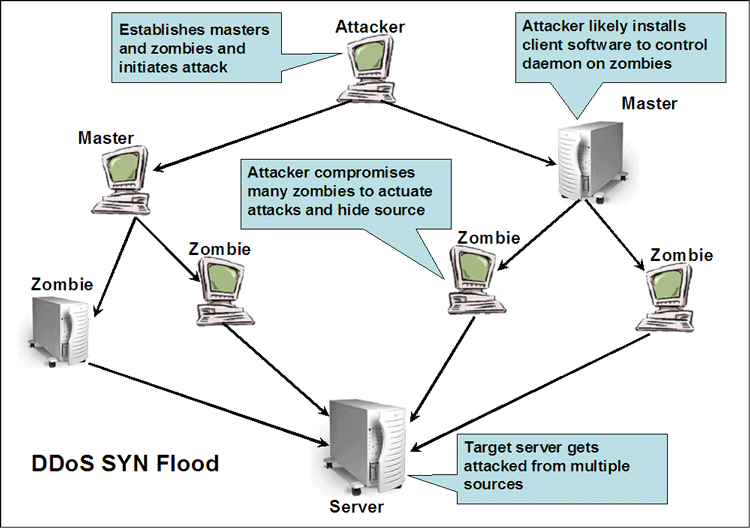
| So a SYN Flood or attack makes use of many
zombies to send SYN packets. While this requires much more
effort to develop and actuate, it should make sense this sort of
attack will be much likelier to prove overwhelming. Ways to Protect. There are a number of ways that have been developed so that administrators can help protect their systems from these sorts of attacks.
|