Spoofing
Some Background.
I want to start with some background and a few definitions.
The main protocol for the Internet, TCP/IP, makes quite a few assumptions about the trustworthiness of those using the Internet. Initially, the protocol was developed to be used for particular researchers to be able to network with certain well known U.S. military systems. TCP/IP was designed so that packets of data and/or information had the source and destination IP addresses included with each packet. But it has proven to be too easy to inaccurately represent the source destination's IP address. Some of the main types of spoofing are listed below.
We will go into more detail about each of these in the following sections. A Bit of Background on IP and MAC Addresses. I'm assuming you have learned about MAC and IP addresses in at least one previous course, likeliest in Networking. So I just want a quick review without many details at all. You can determine your computer's MAC and IP addresses by taking the following steps.
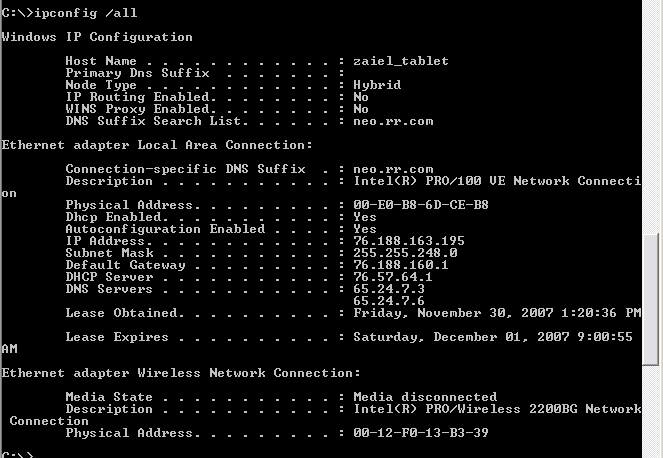
After following these steps you should see something like the following. |

For the computer used to
generate the picture above
MAC addresses are represented in hexadecimal or base 16 so that the letters A, B, C, D, E, F have numerical meaning. When each computer is manufactured it is given a unique MAC address. It has been my experience that networking cards are also given unique MAC addresses. While I have heard that sometimes MAC addresses are used more than once, accidentally, this seems to occur very rarely. But MAC addresses are so unique and relatively hardwired they are often used to determine whether someone should gain access to a particular network, in addition to other approaches such as username/password and/or biometrics. On most networks IP addresses are generated through a DHCP server each time someone logs into a network. Thus, IP addresses frequently change for each machine. Some of the devices on the network, such as DNS Servers and Gateways are much more likely to have static (unchanging) IP addresses. While I could say much more about both MAC and IP addresses, I assume you have learned much more in other courses. Spoofing IP Addresses. Unfortunately, spoofing IP addresses is not as difficult to do as it should be. In fact, source IP addresses may be systematically changed. For example, let us say you have logged into your usual network and received a dynamically allocated IP address from your DHCP server. It is fairly common that when you send packets outside your network, particularly to request some packets be returned, that your network security system will obscure/hide your source IP address. They will likely make use of some sort of more universal IP address for your network when sending your packets so that they CAN'T be as easily traced back to you. Of course, in order to make sure your requested packets get back to you your own network will need some sort of internal way to identify you. But you can rest assured that because of a number of reasons you are not going to have a static IP address that is used externally and traceable back to you by people outside. For example,
More to be written. Spoofing MAC Addresses. This is really quite a bit more difficult than spoofing IP addresses since they are supposed to be "hardwired" into particular components of computers and other network related devices. Since MAC addresses are used primarily at layer 2 of the OSI model generally within access LANs, spoofing MAC addresses is most often used to help gain access to an internal network. Though, there are ways to spoof many networks to grant particular types of access even from outside. Spoofing IP Addresses. Unfortunately, this is not as difficult as it should be. Sometimes it is as easy as changing what is in the "From" entry depending on the software being used. Spoofing EMail. There are a number of ways to do this. Many of these also help for certain kinds of spoofing of IP addresses.
Spoofing Websites. Attackers have been known to create websites that are very similar to other websites. These are most frequently done for sites of the following types
The basic strategy is to trick site visitors into thinking they are at the original/desired site and then also trick them into revealing their credentials such as the following
The developers of these spoofed sites usually create only enough of the site they are trying to spoof to trick visitors into using their credentials which can then be captured/intercepted. Once these credentials have been intercepted, they can be used by the attackers to wreak all kinds of havoc on the user's legitimate account. Phishing. Phishing is based on both email spoofing and website spoofing. The most typical strategy is to send out a mass email/spam that pretends to be from some source that should be trusted by the user. These sources usually pretend to be something like the following
The email must seem believably officious in order to be successful. The email almost always contains one or more links to a website that has been spoofed to help trick the user into entering confidential information that can be intercepted. Once certain credentials have been intercepted, the user is usually redirected to the legitimate website which helps ensure the user doesn't figure out what has happened.
Spoofing and Trusted Relationships. Spoofing can make use of trusted relationships between administrative domains. Once a spoofer has gained access to one administrative domain they may be able to take advantage of any previously developed trusted relationships at higher levels. Though, these relationships should have other safeguards, they often do not. If there are certain sorts of communications or services that are automatically granted to users in another trusted administrative then a less than scrupulous user might exploit these. For example, Spoofing and Sequence Numbers. Spoofing is generally going to be much easier if the attacker can somehow get inside the same administrative domain (network) as the target. Formulating packets that will fool the receiver is more difficult from outside an administrative domain (network) for a number of reasons. All packets must each have an associated sequence numbers. Sequence numbers within an administrative domain/network are much more easily viewed by an attacker. The following list gives several of the rules required for sequence numbers.
Packets do not necessarily arrive in the order they were sent in, nor do they necessarily take the same route to get to their destination. Sequence numbers can be used to help reorder packets and to refer to packets that may have been lost in transmission. The following diagram represents a typical three way handshake along with its sequence numbers. |
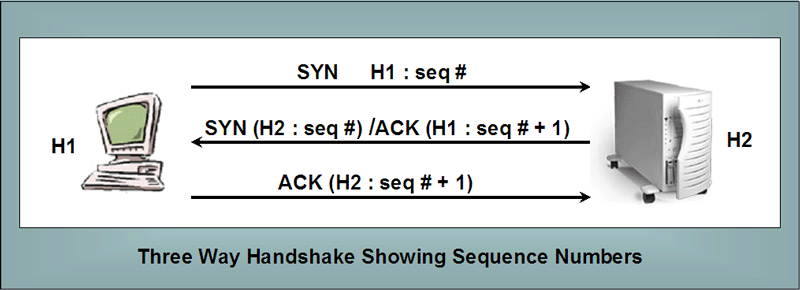
So the more these exchanges are within a network the attacker has penetrated, the easier it is to observe the sequence numbers. Predicting unknown sequence is possible. Sequence numbers from different network communication sessions are generally initiated by incrementing a previous sequence number by some large number. But actually determining these sequence numbering patterns can require quite a bit of observation and/or trial and error by the attackers. Sometimes these initializing numbers are based on the current time, which might help the attacker. So how these sequence numbers are assigned within a system can be determined and spoofed. But it is much more difficult from outside administrative domains/networks. |