Remote Access Security
| Acronyms.
Remote access security can be quite a
mine laden venture. System designers, developers and
administrators need to be able to develop security that works when
users are not within their own trusted domains.
As with pretty much every aspect of networking and security, this subset of security is laden with jargon and acronyms. Throughout this collection of webpages we will cover a pretty large variety of topics including the following.
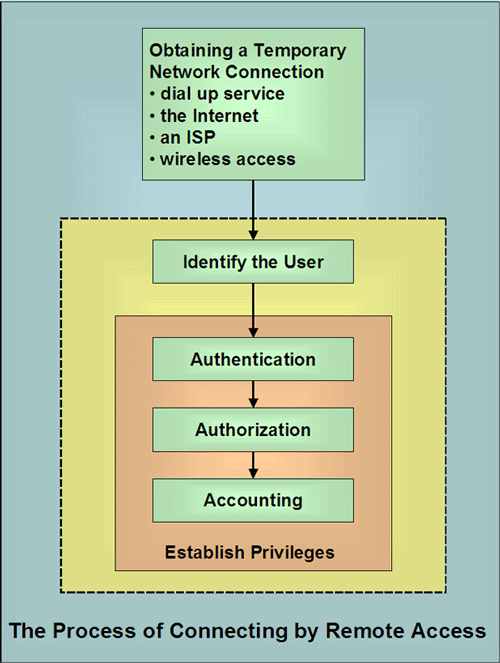
There are plenty of other technologies, particularly relating to wireless. Remote Access Process. In order to examine remote access security, we need to first discuss the remote access process. The process for connecting remotely involves two main aspects.
The following diagram gives a representation of the process. |

|
Identification and Authentication. First the user must be
identified and
authenticated by matching user
supplied information to credentials that
have been previously supplied.
The U.S. Government has published something called the Rainbow Series for computer security. Within this series, the government has suggested there are three main categories of things that can be used to identify and authenticate a user.
In reality, identification and authentication are usually done with the following.
There is the possibility that other things are supplied or done such as the following. Authorization. The next step is authorization where privileges are given based on the authenticated identity. Authorization usually involves the following sorts of issues.
Authorization capabilities are usually built in to an operating system. Though, there are still plenty of reasons to augment and improve built in capabilities. Accounting. The final step accounting relates to the collection of particular information associated with this user's session such as the following.
Improving Validity. Separating these tasks involved in accessing a network has a variety of advantages. Some of the biggest advantages derive from the variety of approaches that can be used at each step. This can allow the system admins to select one or many ways to identify, authenticate, authorize and account in many different combinations with other approaches. It also allows admins greater flexibility in choosing and/or changing their approaches so they are less obvious to attackers. More will be added. |