PPTP
| Some Background.
PPTP - Point-to-Point Tunneling Protocol is a tunneling
protocol that operates at layer 2 of the OSI model. It is
likely the most prevalent tunneling protocol presently in use. Personally, I think it would be much better if they called it PPEP for Point-to-Point Encapsulation Protocol. Common usage says that tunneling is achieved by encapsulation and encryption/decryption. It is my sincere opinion that the word tunneling is inappropriate in a number of ways.
Unfortunately, I have seen many "informed" decision makers talk about tunneling using the bullets above! Encapsulating a packet in another packet can serve a number of purposes
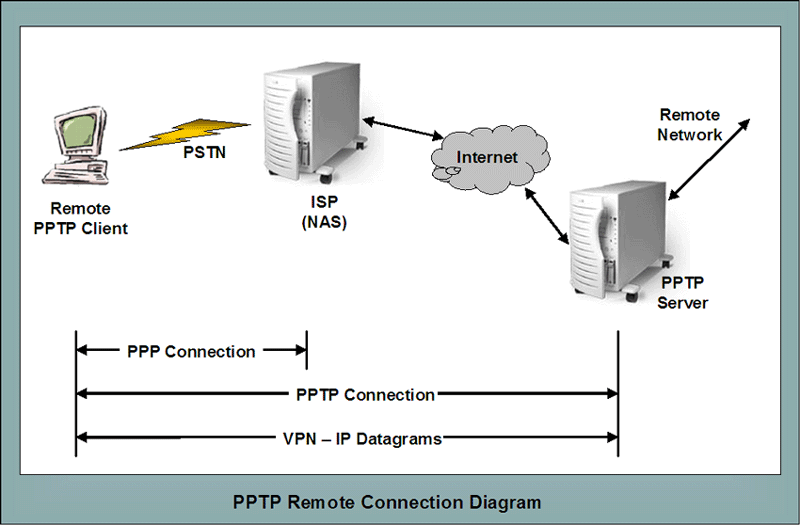
Microsoft's Impact. Microsoft led a consortium of companies to extend PPP - Point-to-Point Protocol to enable VPNs. This consortium is what developed PPTP to enable much greater security when connecting via networks. PPTP can also be used to enable VPNs across the PSTN - Public Switched Telephone Network. For most PPTP implementations there are three computers involved.
This is illustrated in the following diagram. |

The PPTP/VPN is established in stages.
To establish these connections, TCP uses port 1723. So in order for PPTP connections to be established, port 1723 must remain open across the firewalls involved. PPTP allows the use of any PPP authentication approach. CHAP is used when encryption is specified. Microsoft chose the RSA/RCA cipher for encryption. Either a 40 bit or 128 bit session key can be used. The length of the key is determined by the operating system. Other sources say that MPPE - Microsoft Point-to-Point Encryption is used to encrypt data. As is almost always the case, authorities differ.
More will be added. |