Denial of Service Attacks
| Some Background. DoS
- Denial of Service is really a fairly general concept.
It can be quite easy to forget that there are a huge number of
different approaches to deny services on any given system.
In general DoS attacks are attacks that work to diminish the abilities of a system or network to deliver services. It is almost always the case that the attackers are trying to shut down at least certain services completely. But any significant degradation in services needs to be examined for whatever causes them. These attacks can be motivated for a number of reasons. For example,
DoS attacks do not generally require the attacker to penetrate the system under attack. Though, DoS attacks can be made more deleterious if they do. If DoS attacks come from within a system they are generally much easier to trace to their sources. From [Crayton, Dubrawsky, et al]
I should add, that the last I knew, making use of IPv6 required huge capital outlays and annual payments in excess of millions of dollars. Hopefully, this is no longer true. But since IPv6 is not spreading based on its advantages it is very likely due to cost considerations. In the next two sections I will discuss two main types of DoS attacks.
In subsequent webpages I will get into more specific details about particular attacks such as SYN attacks or SQL Slammer attacks. Resource Consumption Attacks. Now I want to say some more about certain types of DoS attacks. It seems almost every system administrator and user is constantly complaining they do not have enough of the following
Some of the most common DoS attacks go after network bandwidth. This is likely due to a combination of limited capacity and accessibility to outsiders. Attacks are generally from outside the system/network for a number of reasons. When an attacker directs a large number of packets at a particular system it is called flooding. If the attacker has more available bandwidth than the targeted network then flooding is more easily accomplished. These sorts of attacks are more easily accomplished as more and more home users make use of DSL or Cable access with increased bandwidth. Some fairly well known types of DoS attacks are listed below.
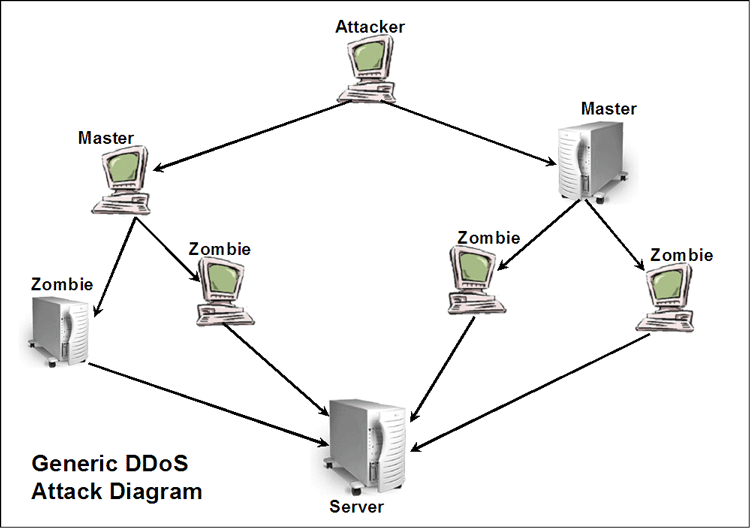
Malformed Packet Attacks. Malformed packet attacks can develop in quite a number of different ways. DDoS - Distributed Denial of Service. DDoS stands for Distributed Denial of Service attacks. There are many different ways these can be used. But they generally rely on an attacker or group of attackers being able to put together a group of zombies to attack some resource simultaneously. We are going to try and present this in general terms in this webpage and get into more specifics for specific types of attacks in subsequent webpages. Organizing a DDoS requires some expertise. The attacker is likely to need at least to generic types of software.
There are four main classifications for the types of computers used in a DDoS.
All of this relies on the attacker finding computers whose security can be breached in order to put this whole DDoS together. The following diagram represents the tiers of a fairly small DDoS. |

A DDoS requires much more
expertise from the attacker. But a DDoS
also allows an attacker to do things such as the
following
So this is a fairly general discussion. We will get into more specifics and ways that the generic DDoS can be used in later webpages. |