Some More Depth on Wireless Security
Background.
Think about some of the different ways you've interacted with wireless
networks.
Now think of some of the other people trying to use these same networks.
Even for these common situations you can see how gaining and limiting access to appropriate computer resources is very important. As we've already discussed in previous pages, this is not necessarily all that easy! So it should be obvious that in different settings it is important to have different sorts of authentication available. Some hotels require you to pay for your connection, others make it readily available for anyone staying in the hotel. The cyber cafe is also quite likely to want to allow nearly entirely open connectability to at least one of its WLANs. But in most instances, network administrators want to limit access to their WLANs. This is what we will discuss in more depth in this webpage. The 802.11 specification explicates two main mechanisms for authentication when trying to limit access to their WLANs.
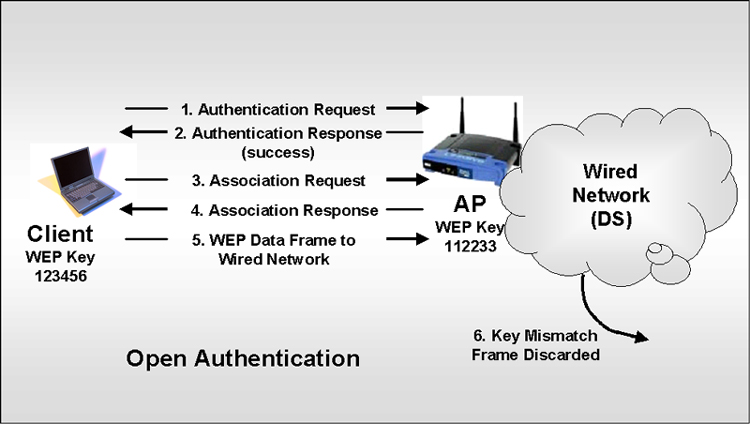
Open Authentication. What is termed open authentication actually requires at least matching WEPs on each client and AP. There still must be some sort of preconfigured WEP. If there isn't, then there will likely be no security whatsoever. The following diagram represents what is termed to be Open Authentication based on WEPs. |

| After open authentication and the association
process the client can begin to transmit and receive data. But
if the WEPs don't match the client will not be able to encrypt or
decrypt data correctly and all such frames will be dropped by both
the client and the AP. If the keys match, then data
transceiving will be possible. Shared Key Authentication. The Shared Key Authentication approach is not all that different from the Open Authentication approach except, that no association is allowed unless a client is able to encrypt/decrypt a challenge correctly. Again, in order for this encryption/decryption to happen correctly the client and AP must have matching WEP keys. The following diagram represents the process for Shared Key Authentication. |
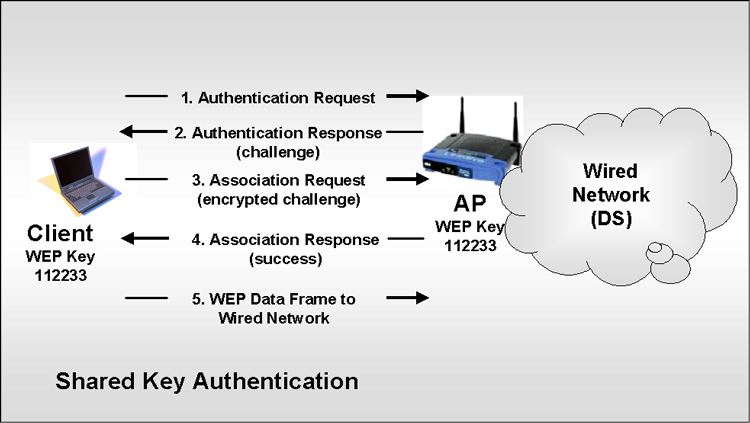
To give some more words of description I've
written out the following.
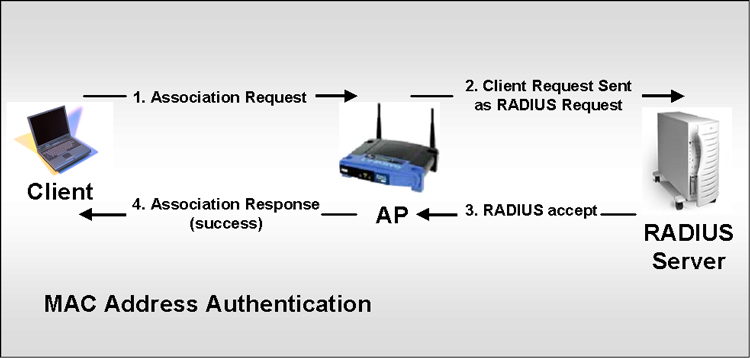
MAC Address Authentication. It should make sense that many organizations want to be able to verify that a client has a MAC Address that is on a specified list. This should really help develop appropriate access to a WLAN. Unfortunately, MAC Address Authentication was not specified in 802.11 so it is only available through particular vendors. This MAC Address Authentication can be done against
Obviously, this sort of authentication could help in a large variety of situations. The following diagram represents the MAC Address Authentication process making use of a RADIUS Server. |
Vulnerabilities.
The 802.11 specifications have some quite well known
vulnerabilities. The following outline summarizes many of
them.
The WLAN industry recognizes these vulnerabilities and is working to develop an IEEE 802.11i standard that will make WLANs both scalable and manageable. But this standard is still not settled and approved. Though I have a source that claims to have very good insights into what will be developing. |