 |
WAN Network Specifications
Introduction.
The basic WAN Technologies can be broken down into two major categories,
Obviously, there is more to these categories than I have just presented. For example, a dial-in user could be a sales rep dialing in to his company's sales database computer. So more precisely,
Looking at this another way, telephone networks have two major ways to provide service
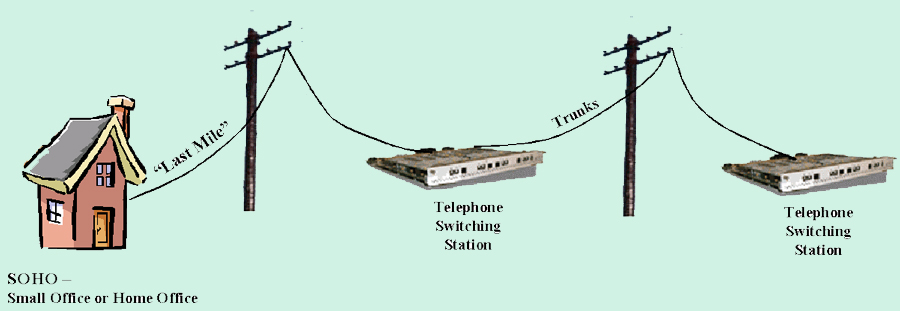
Obviously, the phone companies have set things up so that there is much more capacity between switching stations than there is from an individual home to a switching station. While remembering that "the last mile" is not at all likely to be just a mile, it is much more likely to have a relatively slow telecommunications infrastructure. This last mile has also become one of the major battlegrounds for innovation and attracting new users. The following diagram represents this. |
 |
| The following tables give some of the major options for these types of connections. |
| Last Mile Technologies |
Unmodified Basic Capabilities |
| Analog | 28 or 56 Kbps modem |
| ISDN | 128 Kbps |
| DSL | 640 Kbps upstream 6 Mbps downstream |
| Cable | 384 Kbps to |
| Satellite | High speed downstream No upstream |
| Trunk Technologies |
Unmodified Basic Capabilities |
| T1 | 1.5 Mbps |
| T3 | 45 Mbps |
| Now we will give a somewhat more involved presentation of these different options along with some of their modifications and improvements. |
The Last Mile
| Dial-Up Modem.
This is the standard approach for millions of ISP users on the
internet. Since phone lines are set-up to carry voice/analog
information, the user needs a modem at their end and a modem at the
other end to translate digital signals to analog and vice-a-versa.
The state of art for this gives about a 56Kbps connection working both
for downloading and uploading.
ISDN. ISDN stands for Integrated Digital Services Network. This was set up as the first digital service to the home. It requires a special phone circuit from a local telephone carrier and is often unavailable. ISDN creates multiple channels over one line. A channel is a data path that has been multiplexed over a single communications medium. Multiplexing involves combining multiple signals in a particular way so they can be separated later. The basic ISDN circuit is a BRI - Basic Rate Interface circuit with two payload channels for data. Each channel runs at 64Kbps for a total payload of 128Kbps. There is also a third channel that carries 16Kbps dedicated to network control. Separating payload and control issues improves ISDN's functionality. Another kind of ISDN circuit is a PRI - Primary Rate Interface. It is essentially the same as BRI except it packs up to 23 payload channels, plus one 64Kbps control for up to 1.544Mbps total payload bandwidth. Small businesses make use of PRI circuits, competing at the low end of T1's market niche. DSL. DSL stands for Digital Subscriber Line. DSL runs digital signals over copper wire, though there are plenty of other types of DSL for other media. DSL uses sophisticated algorithms to modulate signals so that much more bandwidth can be obtained from existing last-mile infrastructure. DSL is inherently asymmetric and is configured so that data can be moved much faster for downloading to the client than the other direction. This is actually advantageous in most situations because downloading trafic tends to be much larger. While there are several types we will give a very brief presentation of two of the most popular.
DSL requires a special piece of equipment called a DSL modem to operate. This modem splits signals into upstream and downstream channels. The major difference with DSL Lite is tha tthis splitting is done at the telephone switching station. Cable. A cable modem allows the user to connect to an existing cable television feed. Cable modem download rates range from 384Kbps to several Mbps depending on the service provider and specifications. After much floundering, the industry has unified their operating standards with DOCSIS - Data Over Cable Service Interface Specification. Satellite. Many if not all satellite television delivery systems offer high-bandwidth high speed digital internet access. Unfortunately, all of the speed is in one direction from the satellite to the client. For uploading you need to use a telephone line! |
Trunk Technologies
| T1/T3 Lines.
T1 and T3 digital lines are circuits (or part of a circuit) leased from
a phone company by the enterprise that uses it. These are paid for
by a flat monthly fee regardless of how much it is used. These are
used primarily in North America and Japan. In Europe, the
"equivalents" are E1 and E3.
T1 is the most common and makes use of TDM - Time Division Multiplexing to yield a data rate of about 1.5Mbps. T1 is implemented on copper wire within and between metropolitan areas. If you purchase just a portion of a T1's capacity you are said to have a fractionalized T1. T3 lines are the successor to T1, though they are much more expensive. Their payload capacity is about 45Mbs. Most enterprises that lease T3s only lease fractionalized T3s due to the expense. Last I knew Quinnipiac was leasing a fractionalized T3 with a capacity of about 10Mbps. Frame Relay. Frame relay switches packets of a shared packet switching network owned by a regional telephone company such as MCI or AT&T. Frame Relays usually sit on top of T1 or T3 trunks operated by the provider. Long distance connections are over infrastructure owned by the frame relay provider. These connections are shared among a number of other customers. Most customers rent PVCs - Permanent Virtual Circuits. These give a customer a continuous dedicated connection without paying for a leased line. Frame Relay customers are charged according to level of usage. VPN. VPN stands for Virtual Private Networks. VPN works by creating a tunnel through SVCs - Switched Virtual Circuits that navigate over the internet to reach remote locations. In other words, a VPN runs over shared network infrastructure, but does it in privacy. Encryption is used to create the privacy. To do this, the network segments at each end of the encrypted connections must be under administratie control of the enterprise using the VPN. Typically, an enterprise goes to a high level ISP and purchases SVCs to each of the remote sites within the enterprise. These SVCs assure that routing and security will be optimized. Backup paths are available in case of connection failures. Routers must be configured at each enterprise site to perform the encryption and decryption and handle other aspects of the VPN. The functioning of the routers is very very critical. VPNs are becoming increasingly popular because of cost efficiency, services, reach and flexibility. Many firms are finding that the increased costs for router configuration are more than made up by not spending money for leased lines or Frame Relay service. The major components of a VPN are listed below.
In general, VPNs are estimated to be anywhere from 30% to 80% less expensive than private WANs. This is due to a number of reasons including economies of scale gained from privately sharing resources. Many authors believe that VPNs will soon replace most WANs. |