LAN Network Specifications
| Introduction.
LANs - Local Area Networks are
really the basic building blocks of all internetworks. These
technologies are implemented at the Data Link Layer of the OSI model or
layer 2. This is because these network technologies are largely
determined by the physical media they share and how they control access
to this shared medium. This Data Link Layer is also called the MAC
- Media Access Layer. The basic traffic format at this level is
called a frame.
So, in LANs, communication can only deal with MAC addresses which are serial number like device identifiers. Things like IP addresses are only necessary when routing data across LAN segments through an internetwork. These 2nd layer technologies can only support switched internetwork operations. They are only good for local areas or simple paths over longer distances, where not much guidance to deliver the data is needed. As such, LANs can be classified into two major categories
Some Other Important Issues. Now I want to spend a little time discussing some issues about quality of service QoS. I want to develop these issues at present so we can use them to compare different technologies. Certain types of traffic need predictability more than others. For example, phone conversations can't tolerate delays in transmission because it would disturb the flow of conversation. Video streaming has somewhat similar requirements, though the situation is more flexible. Latency Sensitivity is the term used to characterize these sorts of sensitivity to delays in the transmission. Priority Sensitivity is somewhat similar, but has more to do with the order in which data is received. For example, in video streaming, some small delays are tolerable, particularly with buffering, but if they aren't received in the proper order then there are going to be major problems. A broadcast message goes to every receiving device within a particular domain. Obviously, we all get radio and television broadcasts through different media. Broadcasting on the internet can result in huge overheads on infrastructure demand and is not something generally acceptable. A multicast message goes only to predetermined receiving devices within the broadcast domain. While getting multicasting to work properly is a real problem, it still is going to be preferable to broadcasting on the internet. Ethernet. This is the most common form of LAN. This seems to be due to economies of scale and some other issues that will be presented in this page. It was first developed by Xerox in 1970. Then Digital Equipment Company, Intel and Xerox released a second version often called DIX Ethernet in 1982 an effort to overcome many of the difficulties in the original. Ethernet communications operate by contention. Devices sharing an Ethernet listen for other traffic and transmit only if the LAN is clear. If two stations send at about the same time and their messages collide, both transmissions are aborted and they wait for a randomly generated period of time before retransmitting. Ethernet uses what is called the CSMA/CD - Carrier Sense Multiple Access with Collision Detection protocol to regulate traffic. In addition, because the connection medium is shared, every device on an Ethernet LAN segment receives every message and checks to see whether the destination address matches its own. If there is a match then the message is accepted and processed. If no match is found, the message is dropped. All of this makes it sound as if Ethernet is very inefficient and it is. So much of the available bandwidth is lost to aborted transmissions that the theoretical effective bandwidth is only about 37% of what is actually available! On the other hand, the equipment required to deal with such simplistic protocols is so inexpensive in comparison to other approaches that it ends up usually being the most cost effective. Ethernet has a pretty large variety of implementation options. Three of the most well known are described in the following tables. |
| Ethernet Option | Speed | Connections |
| Original | 1Mbps | coax cable or 10BaseT twisted pair |
| Fast | 100Mbps | 100BaseTX twisted pair or 100BaseFX fiber optic |
| Gigabit | 1000Mbps | 1000BaseTX twisted pair or 1000BaseFX fiber optic |
| A currently popular configuration is to have Fast
Ethernet Access LANs interconnected through a Gigabit Ethernet backbone
LAN.
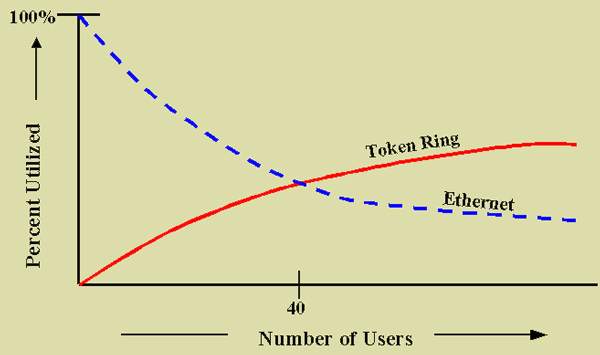
Token Ring. Token Ring used to be Ethernet's main competition. By its own standards it is incompatible with Ethernet in terms of NICs, cable connectors and the software that must be used. Token Ring tends to be most widely used in enterprises dominated by IBM based computing. Token Ring gets its name from the fact that it defines attached devices into a logical, though not likely physical, ring. We call it is logical ring because it passes signals as if the devices were attached by a single looped cable. Physically, they may well be in a hub and spoke layout called a star topology. Token Ring avoids contention over a LAN segment by using a token passing protocol. Only the device in possession of the token is allowed to transmit, thus eliminating collisions. This approach definitely increases Token Ring's effective use of available bandwidth. Testing shows that Token Rings can attain up to 75% of the available bandwidth. Unfortunately, the costs of implementing Token Rings are relatively higher than the costs of implementing Ethernet. It is reasonably estimated that the LAN segments must have at least about 40 users to become cost effective. Once the traffic on a LAN segment increases to certain levels the collisions involved in Ethernet become relatively more costly to the users. The following diagram represents the break even. |

| As it turns out, most LANs are really quite small
mostly because the vast majority of people are employed in small or
medium sized businesses. But even those employed in large
businesses are on LANs that merit the use of Ethernet with all of its
inefficiencies due to things like branch offices or departments in large
buildings.
ATM. ATM stands for Asynchronous Transfer Mode. ATM is actually specified as a Data Link Layer technology on layer 2 within the OSI Reference Model. ATM sends 53-byte cells instead of variable length packets. Using this fixed length results in certain advantages.
ATM is a switching technology in which virtual circuits are set up before a transmission starts. A virtual circuit is built over a path of various hubs, switches and routers. Each end of the virtual circuit must agree to the path before the transmission can happen. This differs from Ethernet and Token Ring which transmit without prior notification or routing determination. ATM's effective yield is well above even Token Ring's 75%. ATM is designed to run over fiber optic cable operating the SONET - Synchronous Optical Network specification. SONET specifications are set up for various cable speeds or OC - optical carrier levels. The following table displays the standard speeds. |
| Name |
Description |
| OC-1 |
52 Mbps fiber optic cable |
| OC-3 | 155 Mbps |
| OC-12 | 622 Mbps |
| OC-24 | 1.2 Gbps |
| OC-48 | 2.5 Gbps |
| Most ATM backbone LANs run OC-3 or OC-12. Most
intercity links run OC-12, although some major backbone providers are
now installing OC-48.
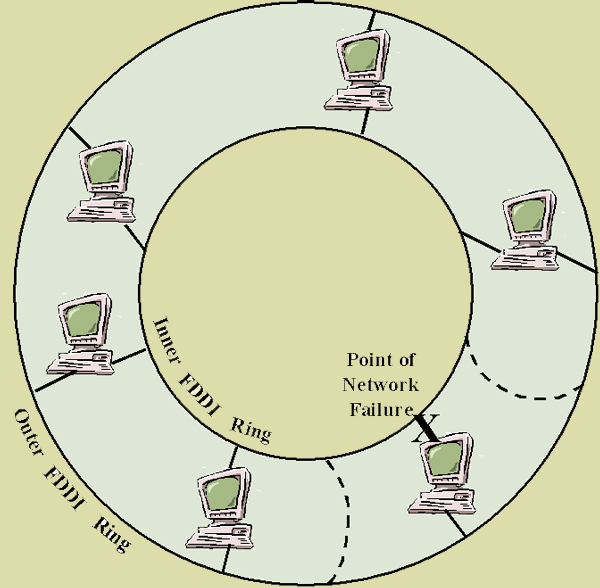
ATM is heavily identified with multicasting of transmissions that have latency and/or priority sensitivities. IN general, its fixed cell format and virtual circuits are much better at dealing with these kinds of issues. As we have already stated, ATM is primarily used for backbone LANs. But at some point, the backbone LAN needs to interact with an access LAN which is almost always running Ethernet or Token Ring. Because ATM deals in cells rather than packets it uses an encapsulation technique called LANE - LAN Emulation to traverse these incompatibilities. LANE is used to break down Ethernet or Token Ring packets into ATM cells on one end of the backbone and reassemble them at the other. While ATM's cost per port is relatively high, its inherent predictability and speed are making it the technology of choice, especially for multimedia applications. Gigabit Ethernet. Gigabit Ethernet is a 1000 Mbps enhancement of the Ethernet standard largely to be used for backbones. The push for it is largely due to its inherent compatibility with Ethernet access LANs. Gigabit Ethernet is the main competition for ATM. It can also scale to WANs. FDDI. FDDI - Fiber Distributed Data Interface is a 100 Mbps protocol that runs over fiber optic cable media. It uses a token passing strategy like IBM's Token Ring so it attains a high effective bandwidth. People have seldom heard of it because it has largely been used for backbones, not access LANs. It has been the network technology of choice for backbones for backbone LANs for a number of years, but is now being superceded by ATM and Gigabit Ethernet. Since backbones are so important to the overall function of networks, FDDI was developed to pretty much guarantee availability. This was done by using dual redundant fiber optic rings. Each device is connected to both rings having two implications.
Under normal operating conditions, the secondary ring is idle, passing only enough frames to keep it running. This secondary ring becomes essential when the primary ring fails. Failures are usually cause by a break in the fiber or a faulty NIC. As the following figure illustrates, FDDI isolates the damaged device by wrapping around to the secondary ring and looping back in the other direction thus keeping the ring intact. |
| FDDI is also now available as CDDI using copper wire.
Network Specifications. The following diagram displays a succinct way to characterize a LAN's specifications. |
| The following table surveys a pretty large variety of LAN specifications. |
| LAN Specification | Description |
| 10BaseT | 10Mbps Ethernet using UTP Cats 3, 4, or 5 cabling. 100 meter limit. |
| 100BaseTX | 100Mbps Fast Ethernet using UTP Cat 5 cabling. 100 meter limit. |
| 100BaseFX | 100Mbps Fast Ethernet using two strands of multimode fiber optic cable per link. 400 meter limit. |
| FDDI | 100Mbps Fiber Distributed Data Interface token passing LAN using either single mode or multimode fiber optic cabling. 100 kilometer limit. |
| CDDI | 100Mbps Copper Distributed Data Interface token passing LAN using copper wiring. 100 meter limit. |
| ATM | 622Mbps Asynchronous Transfer Mode over fiber optic cabling |
| 1000BaseFX | 1Gbps Gigabit Ethernet over fiber optic cabling. |
| 100VG-AnyLAN | 100Mbps Fast Ethernet and Token Ring using UTP Cats 3, 4, or 5 cabling. Can be run over any existing 10BaseT networks. |
| 10Base2 | 10Mbps Ethernet using Thinnet coaxial cable. 185 meter limit. |
| 10Base5 | 10Mbps Ethernet using Thicknet coaxial cable. 500 meter limit. |
| 100BaseT4 | 100Mbps Fast Ethernet using four pairs of UTP Cats 3, 4, or 5 cabling. 100 meter limit. |
| 10BaseFB | 10Mbps Ethernet using fiber optic cabling. 2 kilometer limit. |
| 10BaseFL | 10Mbps Ethernet using fiber optic cabling, used as a LAN backbone, not to connect to hosts directly. 2 kilometer limit. |
| 10BaseFP | 10Mbps Ethernet using fiber optic cabling, used to link computers into a star topology without using repeaters. 500 meter limit. |
| 10Broad36 | 10Mbps Fast Ethernet using broadband coaxial cable. 3.6 kilometer limit. |