Hierarchical Network Design
Background.
Creating some hierarchies in your network design can be advantageous for a
number of reasons. Several of the major ones are listed below.
Using a hierarchical design
The typical model has three layers called
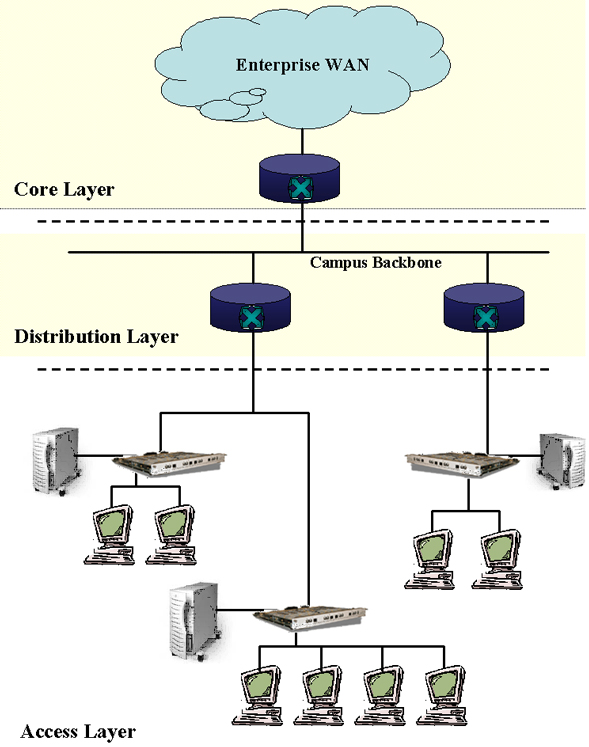
Much more will be said about these in words after the following diagram. |

| The three layers perform three basic sets
of functions in the overall network. While quite a bit more will be
said in the following paragraphs, we will now give a very brief summary.
The access layer primarily grants
access to the internetwork to end users. Typically, switches and/or
hubs are used to create LAN segments. The
distribution layer provides relatively local interaction
between these segments. It can also be used to get what are normally
incompatible LANs to interact. The core
layer provides access to the larger enterprise WAN and the
internet. Now we will say more about each layer. The Core Layer. This is the real WAN backbone layer. It can incorporate multiple backbones from regional ones down to campus backbones. Though campus backbones are more likely to be part of the distribution layer. There should be a minimum of packet manipulation at this layer, they should just be moved without extra overhead. This layer can also be used to limit the diameter of the internetwork and make it consistent regardless of access points . Thus distribution routers and access LANs can be added to the network without increasing the basic diameter or number of hops. The following list is taken from Teare to characterize the fundamental characteristics of a well designed core layer.
The Distribution Layer. This layer is mostly made up of routers. Teare provides most of the content of the following list. A well designed distribution layer should provide the following functionality.
The Access Layer. The access layer is primarily defined by hubs and switches used to segment host devices such as servers, printers and desktops. This layer is also used to improve shared bandwidth, likely by switching. It is also used to provide access for remote sites such as home offices or mobile sales forces. This layer can include routers used to isolate overhead, control traffic and enhance internal security. But this is most likely to happen only in very large networks. |