VPN - Virtual Private Networking
| Introduction.
Think of all the packets routing across the Internet. You might
think you could send your packets to just about anyplace and not worry
about someone else tapping into the flow. Reality is much different.
Particularly, when you think about competitive business environments you
realize that tapping into other firm's data/information flows could be
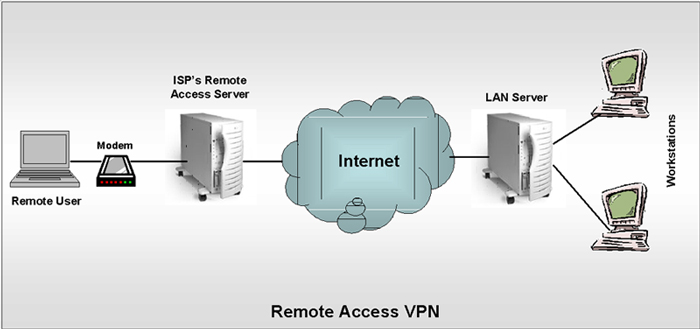
very informative. We have talked a fair amount about internal network security at a fairly general level. Now we need to talk some more about security associated with transmitting packets of information across the Internet. VPN - Virtual Private Networking gets its name from the idea that certain things should be done to increase the likelihood that information gets to only where it should exactly as it was sent. It is intended to help VPN users think/feel that they have a private network tunneled within the Internet. A virtual network gives its user the sense of a direct connection to another location. The privacy component of VPN is based on encryption of the data as it travels across a wider network. Putting these together creates the VPN. VPN can be configured to work through dial up connections or router to router connections on the Internet. Tunneling. In order to develop security in VPNs, a tunnel is created which is essentially a logical point to point connection that supports authentication and encryption of data from one endpoint of the tunnel to the other. Tunneling hides the original packet inside a new packet called the encapsulation packet. For purposes of ensuring the packet can still reach its intended destination a tunneling endpoint is included in the containing packet header. This containing packet header is called encapsulation header. Since the original destination is still contained within the encapsulation, when the encapsulation reaches the tunneling endpoint it can be opened back up to reveal the original destination address. Tunnels can be established at different layers of the OSI model.
Operating System Support. Pretty much all modern operating systems provide support for VPN. This enables VPN connections to servers as easily as those for dialup connections. Windows products after Windows 95 can function as VPN clients using built in components. Windows 9x and Windows NT support PPTP. Windows 2000 supports both PPTP and L2TP. Linux supports supports the use of IPSec and PPTP. You can also create a pseudo tunnel by running a PPP - Point to Point Protocol through SSH - Secure Shell. SSH makes use of the RSA public key technology to authenticate and secure the connection. Why Use VPN? The first thing we want to do is discuss some different scenarios where VPN might well be useful. The following outline about some different VPN scenarios should help.
|

The following table contains some advantages and disadvantages for using VPN in place of dialup networking. |
| VPN | |
| Advantages of VPN | Disadvantages of VPN |
| improves security for connection | both ends must have an Internet connection in order to work |
| can connect through local ISP when traveling | performance is slower than dialup |
| reduce number of incoming telephone lines for remote access | |
| some ISPs offer VPN connections | |