Implementing Security
Implementation.
It shouldn't be surprising that actually implementing security measures is
important. This discussion will focus on two overall strategies.
Authentication and authorization approaches have generally become more accessible through standard releases of operating systems. Old DOS or Windows 3.x releases had next to no security features built-in. Newer desktop operating systems have improved on this considerably. The network operating systems have always had some levels of security features built-in. Though these have also generally improved with each release. User/Group Permissions. Most, if not all, modern operating systems enable an administrator to develop multiple accounts even on desktops. A combination of usernames and passwords allows for limiting access at all levels of computing. Permissions can get even more refined to do things like enable the ability to install software or require virus checks. When a user enters their username and password, several things are likely to happen at least at some broad level. The following list surveys several things that are likeliest to occur to different extents.
When implementing a username and password approach to security many of the following issues are likely to be important.
Access control policies also need to be developed. For example, a user might have read and write privileges on one database in order to do their job, but not on any others. Maybe someone requires permissions to publish webpages for the organization web. Modern NOSs have considerable capabilities for assigning such granular permissions. It is also important for the sys admins to be aware of default and inherited permissions. These sorts of things can cause some inadvertent assignments of permissions. It is important the permissions and authorizations are quite explicitly laid out to help assist the sys admins from making errors. Security groups can assist the assignment of permissions. Groups are created and assigned particular permissions. Then individual user accounts can be placed into these groups, thus saving the sys admin the effort of continually recreating permissions for successive individuals. Encryption. Encryption of information can be of great assistance in ensuring that data isn't understood even if intercepted and/or accessed. File encryption allows a particular user to encrypt desired files on storage devices under their control. This sort of encryption can assist when data is transmitted over a network if the users at the other end know how to decrypt the data. This approach, in and of itself, isn't likely to be the best due to other complications that arise. IPSec - IP Security was created to secure data at a packet level. The ability to decrypt can be known solely at this packet level. IPSec has also been developed to operate purely at the network layer of the OSI model. This allows there to be no need for the specific applications to even be aware of the encryption done for the transmission. IPSec makes use of two protocols that can be used in consort or separately.
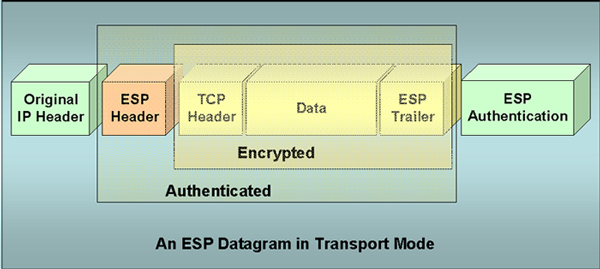
IPSec can operate in two different modes.
The packet headers differ depending on the IPSec mode being used. The following diagram represents a packet sent in transport mode. It is important to notice what is encrypted and what requires authentication in order to be accessed. |

| The next diagram represents the basic contents of a packet sent in tunnel mode. |
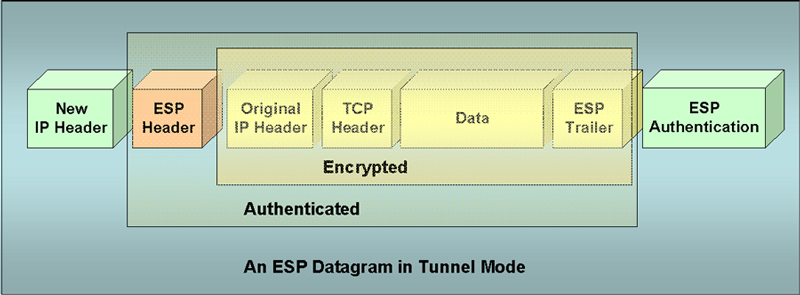
| It shouldn't be very surprising to see the differences
between what can be openly accessed and what has extra layers of security
and encryption. Secure Sockets Layer. SSL - Secure Sockets Layer is another means of increasing security in network communications. SSL operates at the application layer and it must be supported by each particular user application. SSL was developed by Netscape to provide additional security for its web browser. It makes use of public and private key encryption discussed in the next web page. E-Mail Security. Since it is so pervasive, e-mail is what we will try to use to give some more insight into computer network security. Most users assume that the e-mails they send are read only by the recipient. They really are more like postcards that can be read by everyone along the way who handles them. They are somewhat easy to intercept since they often travel through so many different servers and routers along the way to their destination. Even when e-mails are sent on a local network they are likely to be stored on at least three machines.
Internet e-mail can pass through many other devices in addition to these. Unless it is encrypted and signed it can be read, copied or altered along the way. Many different products have been developed in efforts to improve on these sorts of problems. Usually the efforts focus on the following goals.
It is also very important that software associated with e-mail propagation is considered easy to use by its users. Some of the most popular e-mail protection programs include the following.
Most of these programs make use of public key encryption and digital signatures to help ensure data confidentiality and identity authentication. Both of these are discussed in much more detail in the next web page. |