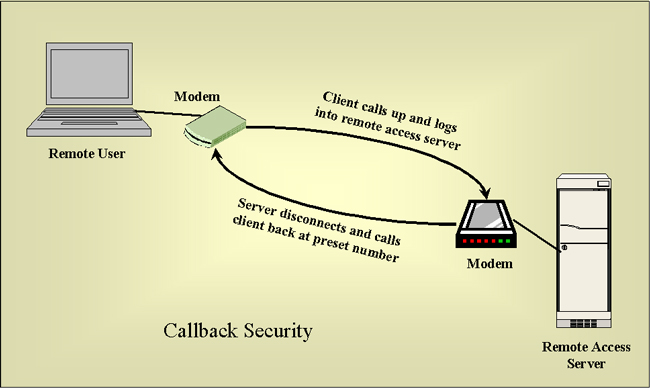
The steps are given in the following outline.
- a preset telephone number along with the user's
account is entered into the remote access server
- when the user dials the server they are prompted
for a username and password
- this verifies the identity of the user and
verifies if they are configured for callback security
- the server breaks the connection and immediately
dials back to the preset telephone number on file
- if the user is actually at this number then the
server enables appropriate access to resources
This process helps ensure the identity of the user.
RADIUS.
RADIUS is a protocol for authenticating dial in users. It has
become an industry standard, particularly for ISPs.
The dialup server needs to be configured as a RADIUS
client. Then the dialup client's username and password are sent to
the RADIUS server by the remote e access server for authentication.
The RADIUS server provides centralized authentication
by using protocols such as the following.
- PAP
- CHAP and MS-CHAP
- EAP
- DNIS - Dialed Number Identification Service
- based on the number called by the user
- ANI - Automatic Number Identification Service
- based on the number the user is calling from
RADIUS also enables the logging of audit and usage
information. It also enables management of remote access servers.
Specifications for RADIUS are provided in RFC 2138 and RFC 2139.
It might be apparent that such an approach allows
remote access servers to be distributed across a large number of
regions, possibly to ensure potential users can almost always make local
calls regardless of their location. But RADIUS ensures that each
server doesn't need to have authentication information for every
potential user.
Remote Access Policies.
As should be expected, it is important to develop policies that help
govern the usage of remote access. Whether or not users can gain
access is likely to need to depend on things such as the following.
- time of day
- day of the week
- group membership
- type of remote connection
A lot of other issues also need to be considered, but
these are policy issues more likely to be associated with remote access.
Account Lockout.
If the sys admins determine that unauthorized users are gaining access
from having somehow obtained a valid password it is likely to be
necessary to lockout the user and/or session. This is most likely
to be done based on the number of attempts someone makes to gain access.
After a particular number of attempts the account is locked out and the
access server won't accept any more attempts.
This sort of feature can be configured in many ways.
Two of the most frequently used ways are in the following list.
- Preset the number of failed attempts before
lockout
- users might accidentally mistype so there
needs to be some leeway
- a most typical setting is for three attempts
- It can also be important to set how long it
take before the account automatically resets.
- the legitimate user might actually attempt to
login
Security Hosts.
A security host is a device used to
authenticate users. These resources are used in addition to the
remote access server's security measures.
These security hosts are actually installed between
the remote access client and the server.
Sometimes these security hosts require the user to
provide an additional username and password for its own purposes.