Some General Background on Network Administration
| Client/Server Environments.
Server based networks require the presence of one or more dedicated
servers. Servers are usually
computers with more than typical amounts of RAM, hard disk space, and
higher processing speeds than the clients that connect to it.
Distribution of servers over a network usually makes it clearly different from much more centralized networks based on mainframes. Typically, in mainframe networks, the mainframe does almost all of the processing for connected terminals. Clients in server based networks often have their own fairly powerful processing capabilities. Having particular services such as e-mail, printing, databases and web hosting on servers tends to make the networking environment somewhat easier to administer. In these sorts of environments, clients request services from the servers. Client/server applications have certain sorts of structures where some operations are done by the client and others are done by the server. The mix is almost never the same from one service to another. The following discussion broadly surveys what is involved in a client making use of Microsoft's SQL Server on a server.
This has the advantages of having the database processing done on a single machine, which is likely faster and more secure. The network traffic is restricted to the request and the solution. Some other advantages of this sort of approach include the following.
While the initial costs of obtaining and configuring a server can be substantial, the benefits easily offset these costs in many situations. Client/Server network configuration tends to have particular characteristics. In particular, for database sorts of applications where data is maintained on a server the network can be configured in one of two fairly general ways.
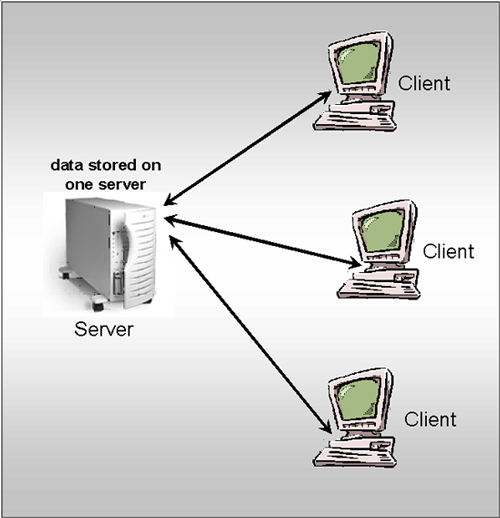
The following image represents data on a single server. |

Think of a small firm that keeps a database on
customers, such as their addresses, phone numbers and past transactions.
They are also likely to have some sort of database for payroll. If
you kept these databases on client machines, for example,
Often times it is the case that the data is either too elaborate, large or has accumulated for different purposes or at different locations over time. In these instances it is likely that you will have no choice but to keep them on separate servers as illustrated in the next diagram. |
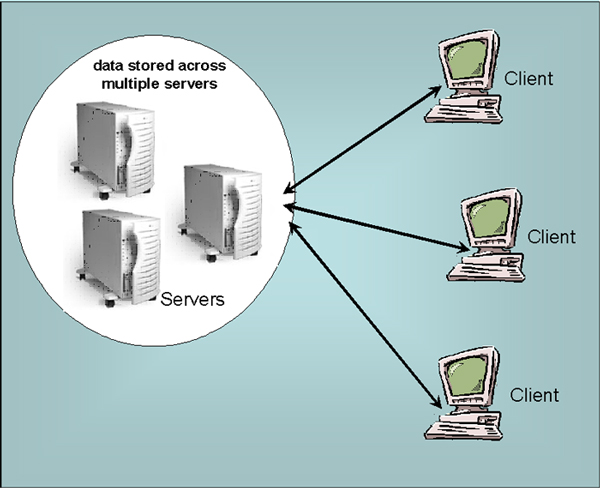
| In this sort of situation you are almost certainly
going to use something called a data warehouse. This allows you to
implement a single interface to interact with these disparate data
sources. Without computer networking this wouldn't be possible. Sharing Network Resources and Security. We have already presented a number of reasons for the desirability of sharing resources on a network. But how this is actually implemented really depends on the NOS -Network Operating System. Novell has most resources configured to be shared by default. Windows platforms require particular resource shares enabled. It should be clear that when services and resources are shared on a network there needs to be some well developed security to help prevent misuse. NOSs must have some sort of capability to set user level security to set the permissions for each user. Implementing such security requires the development of user accounts. Most NOSs allow for organizing these users into groups for easier management. Some NOSs also require that each computer also has an account in order to login when it is used. We now examine three main types of accounts.
User level security requires that each user have their own account. This is usually implemented at the network level, but can also be implemented more locally on particular machines. In general, user level security makes use of user accounts and access control lists. the following gives an example of their interaction.
The exact methods for creating these accounts varies by NOS. As we have said previously, many NOSs allow the administrator to manage user rights by assigning them to groups. This way, the permissions can be set for groups and then all the members automatically gain the same permissions. Consider something as simple as partitioning students, faculty and staff at a university. Obviously, this will become more complicated when determining things like student help desk staff, computing faculty, computing students and database administrator staff. But all in all this is almost certainly going to simplify setting permissions for most individuals. Once groups are developed it is also likely to be able to do things like send group e-mails. NOSs that are designed for higher security environments are also likely to have accounts for devices on the network to validate their presence and capabilities. These are often classified as computer accounts. For example, a sales reps laptop may well be configured to submit information to validate that it has permissions to be connected to a particular network. Managing Shared Resources. After presenting some general background we will discuss several different types of shared resources.
In some NOSs when you create a shared resource it is by default accessible to the Everyone group, which contains all users. If this is not what is desired then it is necessary to modify the permissions. Shared resources are generally given share names which are quite representative of the function of the resource. This can be particularly important when implementing an upgrade. It is surprising how important these names can end up being. Unfortunately, two of the main purposes of security relative to shared resources are somewhat contradictory.
These objectives are usually accomplished using something called directory services which will be developed in web pages in the future. It can be very important to implement some capabilities for sharing files and folders across a network. As we have generally discussed relative to databases, it can be important to make sure the appropriate users can access, read, and/or write to the most up to date files and folders. It can be very important to not rely on copies on a variety of user's hard drives. You could have a single person in charge of the document keep it resident on their computer, but this results in different types of problems.
In some operating systems, shared folders can be mapped as a network drive to increase its accessibility to those that have appropriate authorization. Peripherals, such as printers, can be very expensive. It is important that they are utilized and accessible. An application server can allow authorized users to access particular applications. Sometimes, only one copy needs to be maintained on a server if it is reasonable to run the program across the network. This will definitely be true for things such as most database applications. Making use of application servers for some resources can result in a number of benefits such as the following.
Shared connections can improve the access and utilization to things such as the Internet. Instead of each user having slower, less capable connections such as modems and telephone lines, all networked computers can connect through something of much higher quality. There are several ways such connections may be implemented such as the following assuming the connection to the outside is of desirable capacity.
All of these approaches also improve security. |