Some More on IP Addressing
Background.
Now we need to present a variety of issues that need to be dealt with in
order to adequately implement IP addressing. We have already
presented some background on addressing and discussed how there is a
shortage of available addresses that work entirely within the standard IP
address configuration. The following list outlines the major issues
we will address in this webpage.
This ends up being quite a diverse list and it doesn't tie together as well as I'd like. Thus we will jump around even more than usual. Automatic Address Allocation. To communicate using TCP/IP every device on the network must have a unique IP address. This address is most likely a logical address rather than a physical address. The following are two very general rules that must hold for any IP addressing scheme.
We have discussed how classless addressing can definitely improve our options. We have also discussed how using private addressing along with some sort of internal address translation can be used to improve our options. But before delving into these in greater depth we need to describe the two ways to obtain an IP address.
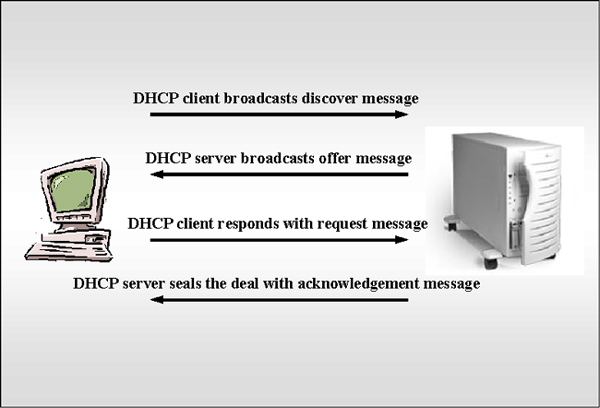
DHCP DHCP is a protocol that has been designed to allocate IP addresses to machines that are configured as DHCP clients. The following figure illustrates the communication process. |

The steps involved in this interaction to obtain IP
addresses from a DHCP server are outlined in the following list.
When all of these steps are completed, the client can use the IP address to communicate with other devices using the TCP/IP protocols until the lease on this address expires. The duration of the lease can be set by the DHCP server administrator, but it is often for the duration of a network login session. Sometimes, the client can negotiate with the DHCP server to extend the lease duration. Normally, the DHCP will be configured to grant such requests. But, in particular, if the DHCP server has gone offline or sends a NACK - Negative Acknowledgement then the client must go through the process all over again. DHCP has many advantages over manual IP addressing by system administrators such as
Sometimes it is necessary to configure a device so that it uses the same IP address whenever it is on the network. In this instance, you can still use DHCP but the device must be configured with a reserved address or static IP address. This address is usually directly based on the MAC address of the device. The DHCP server will always assign the same IP address to such a device whenever it is on the network. This is particularly common for servers. DHCP can be used with just about all operating systems including Microsoft, UNIX and NetWare. Unfortunately, different vendor's implementations are likely to have their own idiosyncrasies. APIPA Another way to automatically obtain IP addresses is APIPA. APIPA was introduced to circumvent the problem of a client obtaining an IP address when no DHCP server is available. This way a device can assign itself an address from the available range of addresses. This self assigned address can be used until the DHCP server is again available. TCP/IP implementations on Microsoft products such as Windows 98 and Windows 2000 include this feature. Subnetting and Supernetting. Subnetting involves borrowing some of the bits associated with the host address and using them to consolidate a portion of the network into a subnet. Thus, when subnetting, a routing device needs to be able to determine
One of the more common ways to denote what is used for the subnet mask is entered by the sys admin into the TCP/IP properties. A subnet mask is represented by a 32 bit number where the contiguous 1s are used to denote which bits are used for the network and contiguous 0s are used to denote which bits will be used for the host device. The following table contains the default subnet masks for the standard IP address classes. |
| Address Class | Binary Subnet Mask | Decimal Subnet Mask |
| Class A | 11111111.00000000.00000000.00000000 | 255.0.0.0 |
| Class B | 11111111.11111111.00000000.00000000 | 255.255.0.0 |
| Class C | 11111111.11111111.11111111.00000000 | 255.255.255.0 |
| In reality, these subnet masks currently represent
unsubnetted networks, which is an unfortunate result of the
terminology. What happens if we want to subnet a network? Let's assume we want to divide our local network into six subnets. Now we need to borrow bits from the host portions of the IP addresses. Thus we need to determine how many more bits we need to use to communicate this in the subnet mask. The following table tells us how many subnets we could specify using a particular number of additional bits. Further in the past, it wasn't good to use all 0s or all 1s in a section denoting a subnet. More recently, it is possible to use all 0s or all 1s. |
| Number of Bits | Subnet Addresses - Currently | Subnets in the Past |
| 1 | 21 = 2 | 2 - 2 = 0 |
| 2 | 22 = 4 | 4 - 2 = 2 |
| 3 | 23 = 8 | 8 - 2 = 6 |
| 4 | 24 = 16 | 16 - 2 = 14 |
| 5 | 25 = 32 | 32 - 2 = 30 |
| Again, we subtract off two potential subnet
addresses due to not wanting to use all 0s or 1s for a particular
subnet address. From this table we can see that we need to take three additional bits from our host addresses in order to specify the subnets. So now if we were working with Class B addresses the subnet mask would be 11111111.11111111.11100000.00000000 Where the positions in the additional 111 triple will be used to specify the 6 different subnets. 001 Unfortunately, by taking away some of the bits from the specification of the hosts, we diminish our capacity to uniquely specify a larger number of them. So now since we have only 13 remaining 0s for identifying hosts we are restricted to 213 - 2 = 8190 hosts on each subnet. The following list outlines many of the advantages of subnetting.
We have neglected to mention ANDing for determining if particular devices are in the same subnet. This might be covered in class. Ports and Sockets. What happens if two network applications running on the same device are sending and receiving packets at the same time? Remember that an IP address is used to route the messages to particular devices. Port numbers are used to route messages within the device to ensure there isn't confusion about what packets go with what message. Port numbers are used as add ons to the IP address. They are used by TCP and UDP to identify the specific application that is sending or receiving the message. Common internet applications have predefined port numbers. This sort of standardization makes communication easier. These assigned port numbers are called well known ports and contained in the following table. |
| Application | TCP Port | UDP Port |
| FTP - Data | 20 | |
| FTP | 21 | |
| SSH | 22 | |
| Telnet | 23 | |
| SMTP | 25 | 25 |
| TIME | 37 | 37 |
| TACACS+ Login | 49 | 49 |
| DNS | 53 | 53 |
| TACACS+ Database | 65 | 65 |
| HTTP | 80 | 80 |
| Kerberos | 88 | 88 |
| POP3 | 110 | 110 |
| NNTP | 119 | 119 |
| NetBIOS name service | 137 | 137 |
| SNMP | 161 | 161 |
| IRC | 194 | 194 |
| LDAP | 389 | 389 |
| NetWare over IP | 396 | 396 |
| Apple QuickTime | 458 | 458 |
| ISAKMP | 500 | 500 |
| rexec | 512 | |
| UNIX rlogin | 513 | |
| UNIX Broadcast Naming - rwho | 513 | |
| UNIX rsh and rep | 514 | |
| UNIX SYSLOG | 514 | |
| SSL Shell - SSHELL | 614 | 614 |
| L2TP | 1701 | |
| PPTP | 1723 | 1723 |
| RADIUS - authorization | 1812 | 1812 |
| RADIUS accounting | 1813 | 1813 |
| There are 65,536 usable ports. Ports 0 through
1024 are reserved as well known ports. A socket is the endpoint of a connection. You must have a socket in order for communication to happen. Different socket types use different addressing methods. The most common approach is to use an IP address combined with a port number. In UNIX this is called AF_NET addressing. Another UNIX approach called AF_UNIX uses pathnames to identify sockets. BSD - Berkeley Sockets became the standard for TCP/IP communications. Winsock - Windows Sockets are loaded as a DLL - Dynamic Link Library in Windows operating system platforms. If you have multiple versions of an application open, such as Internet Explorer, packets associated with an HTTP request will be configured to use port 80. But how will your system know which of the open Internet Explorer sessions should be receiving the packets? This is done using a different socket designation for each port. Addressing in Packet Headers. When communications occur over networks, the addresses need to be available in relatively standard ways in order to facilitate their success. Remember, each layer of the OSI Reference model encapsulates information into packet headers before sending the packet on. These sorts of headers are used in TCP/IP communications to ensure the correct source and destination addresses are passed along in addition to a large variety of other information. By default, IP headers are 20 bytes in length. These headers contain fields that indicate the following.
The following diagram gives a more visual representation of a typical IP header containing 12 fields plus options. |
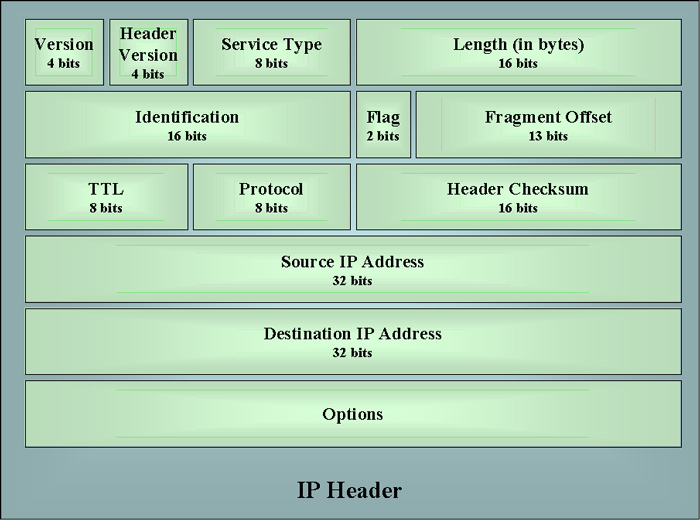
The options can include things such as
The IP header without options will be 20 bytes in length. Name Resolution. Remember TCP/IP makes use of addresses composed of network bits, subnet bits, host bits and ports to resolve difficulties in locating sources and destinations. On the other hand, people prefer names instead of obscure numbering schemes. For example, think of remembering and IP address such as 193.234.23.5 to go shopping. It is much better to remember a simple and mnemonic URL. Standard names on the Internet involve some sort of top level domain type identifier such as those contained in the following list.
Outside the US there are also designations that specify sites with particular national origins such as the following.
Specific organizations or individuals can register second level domain names. this used to be done by InterNIC, but it has been recently distributed to other organizations. The following are three of the most widely used approaches to translate names to IP addresses.
HOSTS and LMHOSTS In the early days the way to match domain names with IP addresses was through a HOSTS file usually on the client's computer. This worked reasonably well, except every time a new site was added the HOSTS file needed to be modified. In addition, in order to make certain this site was available to everyone, the HOSTS file would also need to be updated on every computer on the network. It should be obvious that this was worse than cumbersome. LMHOSTS did something quite similar on Microsoft networks. We won't go into more detail because this is largely a technology that has gone out of use. DNS and DDNS DNS - Domain Name System was devised to overcome the problems associated with using HOSTS. DNS Servers store databases of IP addresses associated with particular host names and URLs. A hierarchy of DNS servers exists on the Internet. Each server contains information for its own zone. If a particular DNS server doesn't have the IP address associated with a particular domain name it can pass it to another DNS server. The following diagram gives a representation of the process. |
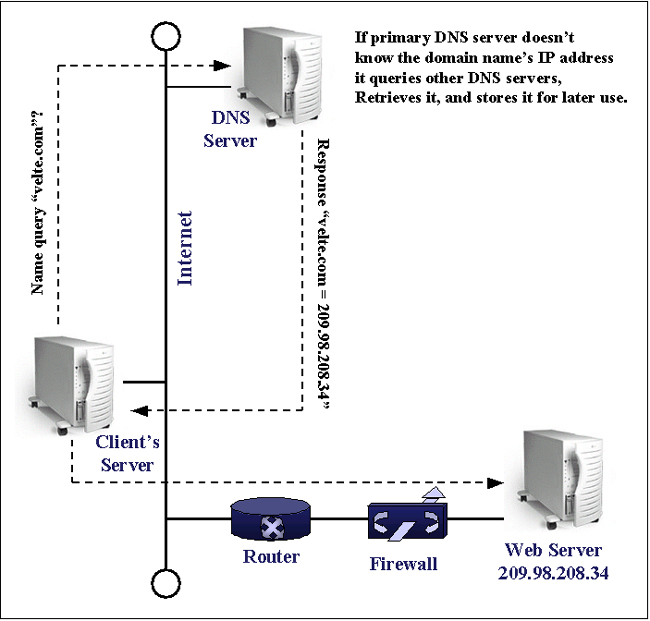
| When you type a URL into the address field of your
browser an accurate and unique domain name such as velte.com needs to be
resolved with a unique IP address. This is done at the nearest DNS
server to translate the URL to an IP address. The IP address for
velte.com is 209.98.208.34, which is the decimal equivalent satisfying
the criteria for IP addresses. The routers and switches that run
the internet don't recognize domain names. The IANA issues IP
addresses. DNS is a big improvement over HOSTS. But even with DNS the server's tables must be updated manually. This motivated an enhancement called DDNS - Dynamic DNS where automatic updates of the database tables are enabled. DNS database tables have a variety of different types of records. The following list contains three of the most common.
WINS WINS - Windows Internet Name Server is another method for resolving domain names with IP addresses. This is done for NetBIOS names on Microsoft networks. These NetBIOS names are mapped in a database on a WINS server. Windows NT and Windows 2000 can function as WINS servers. Since TCP/IP doesn't understand NetBIOS names, this is necessary. But WINS actually uses a dynamically updatable database, unlike DNS. When WINS clients come onto the network they announce themselves to the WINS server with their names and IP addresses. The WINS server builds the database from this information. DHCP, DNS and WINS can actually all work on the same network. In Microsoft's most recent server operating systems these three services have already been integrated to interoperate efficiently. |