Network Communication Concepts
| Packets.
Now when we actually transmit data across networks it needs to be in some
form that can be recognized by the devices on the network. Since the
CPUs of these devices are all operating in binary or digital formats we
need to be able to transmit these or convert them into something else and
convert them back. This is why we sometimes make use of modems which
convert digital signals into analog signals and back when we make use of
typical telephone lines for transmissions. We also want to make certain we aren't tying up our lines as we send data streams. If we preoccupy a line with just one web transmission like is done for telephones we usually end up wasting a resource. This is particularly true because the capacity of the lines should be much greater than what a single user is almost always going to want to transmit/receive. For example, you don't want to tie up the line as someone writes an e-mail message. You want to wait until the user develops the message, reviews it and then sends it. This way you have a lump of data to send. In addition, you want to be able to handle lumps of data from many users pretty much at the same time. This results in lumping data into what are called packets. This will also be important for very large transmissions such as sending a large report with images to a destination. It can be very worthwhile to break this up into smaller chunks in order to make certain connection resources aren't wasted. Some of the major advantages of making use of packets are in the following list.
Unfortunately, this can result in some problems.
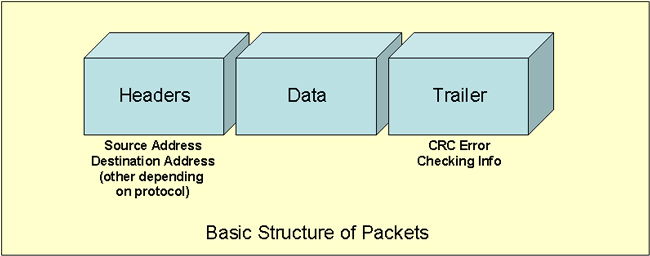
These are issues that need to be dealt with in order for the packets approach to work. In particular, throughout this course we need to discuss how routers making use of TCP/IP have been developed to address these issues. There are plenty of other issues to address, but we will start with how information can be taken apart into packets and how they can be put back together. Taking It Apart/Putting It Together. Now we need to discuss the strategy for separating data into packets and making sure it can be put back together again. When data is broken into packets each packet is given a packet header. These headers contain addressing information so that each packet can get to the correct destination. They also contain information that allows them to be resequenced and put back together when they reach their destination. The packets also have trailer information that relates to error checking to make sure the packet is what was originally sent. The error checking component is what is called a CRC - cyclical redundancy check. If the results of these calculations are different at the reception of the packet than when the packet was transmitted then this particular packet needs to be resent. While this is not a perfect approach to determining if the signal somehow was changed or misinterpreted, it certainly helps. |

| The exact ways the header and trailers are developed
depend on the networking architecture and protocol. In Ethernets the
data unit is called a frame and it can be anything between 64 and 1518
bytes in size. A Token Ring packet is usually quite a bit larger
holding 4202 bytes of data. Layered Communications Process. Getting computers to function conceptually at the levels of 0s and 1s likely seems very involved to most. It gets even more complicated when trying to get one computer to communicate with another across a network. For example, each computer may have a different operating system, and different network segments are likely to have different operating systems. Now we will try to develop some analogies to assist you in understanding some of the overall strategies used to achieve network communications. One of the most important aspects to consider in network development is the variety of expertise's one must have acquired and continually acquire. For these reasons and many others it is often crucial to have a network team so that particular individuals can focus on developing their expertise and contribute to a greater effort. Developing a useful amount of focus for individual team members can have many advantages, a few of which are listed below.
A layered communications process works in a similar manner. Each layer is used for a particular process or task. For example, one layer of the process takes responsibility for interacting with the user. Another layer is responsible for getting the data out of the computer onto the network and packaging it for transmission. Other layers are associated with locating and routing to the destination. Another layer has responsibilities for ensuring the transmission is received and reported back to the source appropriately. Ensuring all of these sorts of things is lumped together under the label of a communications protocol. We have already talked about the OSI Model - Open Systems Interconnection reference model which is still the basis of this sort of approach. The next web page will go back over some of what we have already presented and develop some other issues associated with this model. |