Some Web Database Issues
Introduction.
Up to the present I have jumped around waving my hands and moving my
mouth in hopes that I am developing some motivation for this course.
If you use the web you almost surely have experience with web databases.
Some of the most typical examples are
But there are plenty of other situations where they can be useful. Think about trying to gather information within an organization to do things like
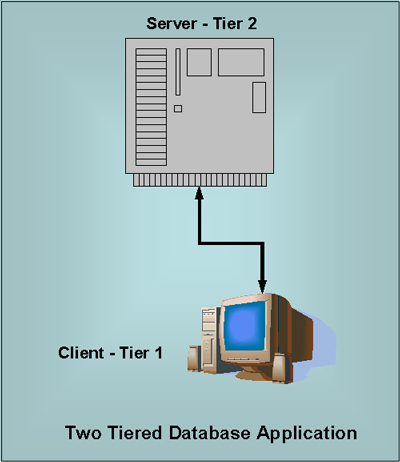
These are just a few other examples. But it should be clear that the only uses for web databases are not for e-commerce stores! They can be used in a large variety of ways to improve both internal and external operations in an organization. Accessibility and Security. One of the nicer aspects of putting databases on servers on the Internet is that they can be accessible from anyplace on the Internet. While the implementers need to be seriously concerned about security and who can access and alter what, this is a great advantage. A typical way to configure such database systems is by putting the databases on the web server in what is called a two tiered approach. This is represented in the following diagram. |

| One way to improve security and overall functionality is with something called the three tiered hierarchy. This is represented in the following diagram. |
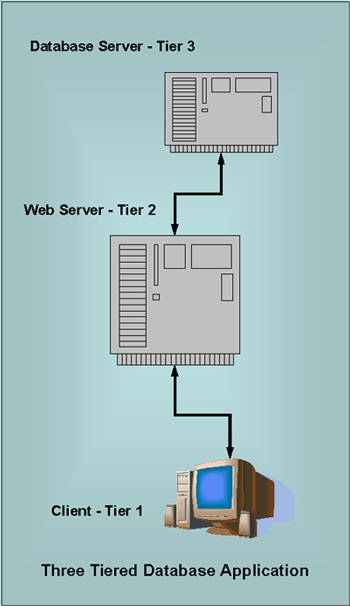
This three tiered approach has a number of advantages.
In this sort of setting, with two and three tiered web database applications running in a Linux environment, the web server running Apache can
The database server, likely running MySQL can
This sort of approach, making use of PHP as middleware ensuring coordination of results with client requests is quite prevalent on the Internet. It also keeps packet sizes and network traffic volume much smaller than it would be in most other configurations. You also see analogous approaches being implemented with things like JSP or ASPs as the middleware using different web server and database server software. It is also likely that the developer will have some sort of scheme developed so that anyone who tries to access certain pages or data is required to have particular authentications. This can be implemented in a number of ways and is something we will discuss at different points in the course. Hosting. Who should be hosting these sites? This obviously depends on the situation and the expertise of the organization. But one of the biggest advantages of using PHP and MySQL is the plethora of potential hosting options. The price of the software is also very good, though expertise always costs money! |